Duo Passwordless
With Duo Passwordless, you no longer have to remember or type in long, complex passwords when you access applications. Instead, you can log in with a single gesture, like scanning your fingerprint. Duo Passwordless uses removable security keys and biometric authenticators built into computers, phones, and tablets to secure access to your applications without passwords.
Contents
- About Duo Passwordless
- Set up Duo Passwordless
- Duo Passwordless Login options
- Touch ID on a Mac
- Face ID or Touch ID on an iPhone or iPad
- Passkeys
- Windows Hello
- Android Biometrics
- Security Keys
- Duo Push
- Log in with Password
- Change Remembered Username
- Remembered Devices
- Set up Multiple Authenticator Types
- Log in From a Different Device or Browser
- Access Device Software Checks
- Device Verification with Duo Mobile
About Duo Passwordless
Duo Passwordless works with applications that use Duo Single Sign-On (SSO). Instead of typing your password on the Duo SSO login page, you'll use your device to verify your identity.
If you change devices, access an application that doesn't use Duo Single Sign-On, or if the passwordless verification method isn't available when you are logging in to an application — such as if you forgot your registered security key, you are using a different browser that doesn't have your push cookie, or you've closed your laptop so you can't scan your fingerprint — then you will enter your password to log in to the application.
Supported Authenticators
Duo supports these passwordless authenticators:
- Platform authenticators: These are authentication methods built into the device you use to access services and applications protected by Duo. Examples of platform devices would be Touch ID on Mac, Face ID on an iPhone, Windows Hello, and Android biometrics.
When you set up one of these methods, it's effective only for the system where you set it up. If you were to set up Windows Hello to log in to Duo Passwordless on one computer, then switch to a different Windows computer, Windows Hello on the second computer won't log you in to Duo. You will need to use your username and password to log in on that second computer, and complete Duo two-factor authentication to access the application, or to set up Windows Hello for passwordless on the new computer.
- Roaming authenticators: These authentication devices are WebAuthn FIDO2 security keys with biometric or PIN verification, like those from Yubico or Feitian. They can move from one system you use to access services and applications protected by Duo to another, such as a USB security key you unplug from one laptop and plug into another.
- Duo Push: This lets you approve a login request pushed to Duo Mobile on your Android or iOS device instead of entering a password. Your phone's security settings must require biometric identification (like Face ID or fingerprint), PIN entry, or passcode entry to unlock the device. When you approve a Duo Push request for passwordless login, you will need to perform biometric or PIN/passcode verification to finish approving the login request.
If you already activated a device for Duo Push in order to perform two-factor authentication, or if you perform first-time enrollment during Duo Single Sign-On login and enroll Duo Push as an authentication method, you can use that same device for Duo Passwordless authentication without repeating the enrollment process. The first time you use Duo Push for passwordless login in a given browser you will need to also enter a six-digit verification code into Duo Mobile.
Duo Push authentication for Duo Passwordless is enabled for the specific browser on the access device you use to log in to with Duo. For example. when you log into an application with Duo Push allowed for Passwordless using Chrome, Duo sets the a passwordless push browser cookie for Chrome on that device and checks for it the next time you log in. If that cookie wasn't saved or if you switch to Firefox on that same device then you will need to log in with your password and Duo two-factor authentication.
Supported Browsers
Duo Passwordless supports Chrome (Desktop and Mobile), Firefox, Safari (Desktop and Mobile), and Edge. Not all browsers support all verification methods on a given operating system, so for the widest compatibility we recommend Chrome or the browser that came with your operating system.
Check the tables below for supported browser versions and Duo verification option compatibility. While other browsers may work with Duo Passwordless, Duo actively tests and supports the browser minimum versions listed in the tables.
The availability of any given passwordless authenticator type when using a supported operating system and browser depends on whether your organization allows use of that type of authenticator.
Your access device's browser must be able to store cookies to use Duo Push as a passwordless authenticator.
Windows 10 and Later
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Edge | 79 | Yes 1 | Yes | Yes |
| Chrome | 73 | Yes 1 2 | Yes | Yes |
| Firefox | 66 | Yes | Yes | Yes |
- Windows Hello is not supported in Chrome Incognito or Edge InPrivate browsing sessions.
- Use of passkeys as platform authenticators requires Windows 11 and Chrome 108 or later.
macOS 11 and Later
You must sign in with the same iCloud account and enable iCloud Keychain sync on all the Apple devices you plan to use with Duo and passkeys. See the iCloud documentation for instructions specific to your device types:
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Safari | 14 | Yes 1 | Yes | Yes |
| Chrome | 70 | Yes 1 | Yes | Yes |
| Firefox | 114 | Yes 2 | Yes 3 | Yes |
- Use of passkeys as platform authenticators requires macOS 13 and Safari or Chrome 108.
- Firefox 122 or later is required for platform authenticators.
- Firefox on macOS cannot prompt to create a security key's PIN. Security keys that already have a PIN set can be used to authenticate in Firefox.
iOS/iPadOS 16 and Later
You must sign in with the same iCloud account and enable iCloud Keychain sync on all the Apple devices you plan to use with Duo and passkeys. See the iCloud documentation for instructions specific to your device types:
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Safari | 16 | Yes | Yes | Yes |
| Chrome | 95 | Yes | Yes | Yes |
| Edge | 95 | Yes | Yes | Yes |
| Firefox | 68 | Yes | Yes | Yes |
Android 11 and Later
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Chrome | 95 | Yes 1 | Yes 2 | Yes |
| Firefox | 68 | Yes 3 | No 4 | Yes |
- Passkey support with Google Password Manager.
- Chrome on Android 11 cannot prompt for the security key's PIN to fulfill the passwordless user verification requirement.
- Firefox on Android 11 does not support Android biometric enrollment.
- Firefox on Android cannot prompt for the security key's PIN to fulfill the passwordless user verification requirement.
Linux
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Chrome | 73 | No | Yes | Yes |
| Edge | 79 | No | Yes | Yes |
| Firefox | 114 | No | Yes | Yes |
ChromeOS 108 and Later
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Chrome | 108 | Yes | Yes | Yes |
Language Support
Your browser's language settings determine the language shown in Duo Passwordless, with no extra configuration necessary.
Supported langauges: Catalan, Chinese (Simplified), Chinese (Traditional), Czech, Danish, Dutch, English (US), Finnish, Hindi, Indonesian, Italian, Korean, Norwegian, Polish, Portuguese (Brazil), Portuguese (Portugal), Swedish, Thai, Turkish, and Vietnamese.
Set up Duo Passwordless
When you log into a Duo Single Sign-On (Duo SSO) application that supports passwordless authentication, you will log in with your username and password, and complete Duo two-factor authentication. See the Duo Single Sign-On guide for an example.
Automatic Passwordless Registration
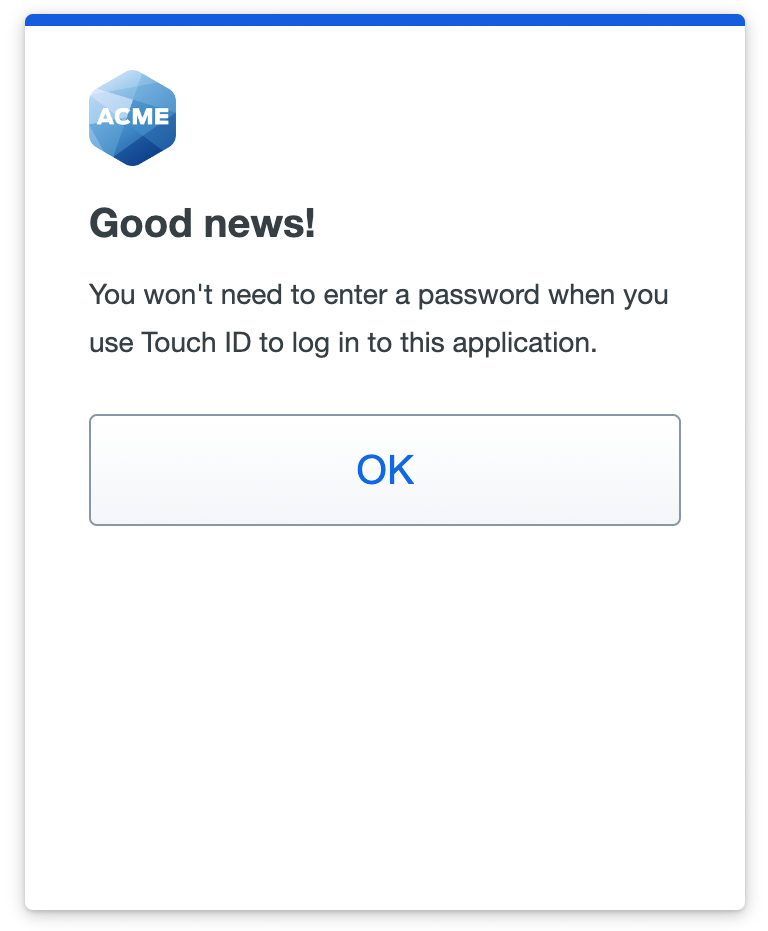
If you sign in to Duo SSO using a platform authenticator for two-factor authentication, such as Touch ID or Windows Hello, then you'll automatically be able to use that same authentication method for Duo Passwordless login in the future without any further setup.
Interactive Passwordless Registration
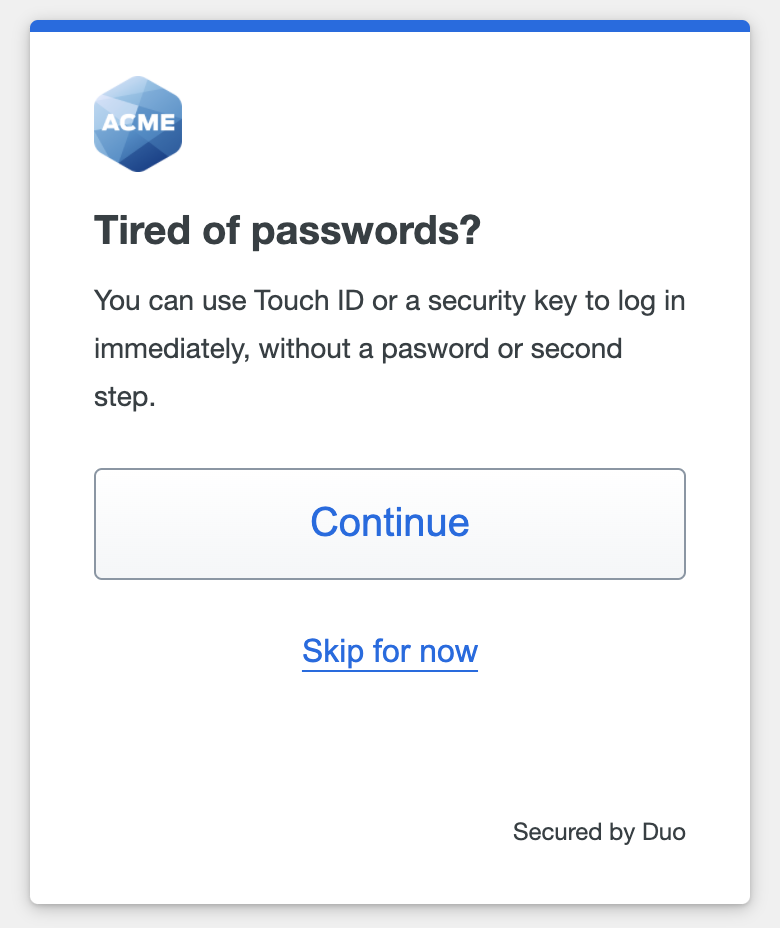
If you log in using any other authentication methods, like Duo Push, you'll see the "Tired of passwords?" invitation to set up Duo Passwordless. Click or tap Continue to set up passwordless login.
If you don't want to set up passwordless login now, click or tap Skip for now to delay the passwordless setup prompt for seven days in that browser. Duo will finish logging you into your application.
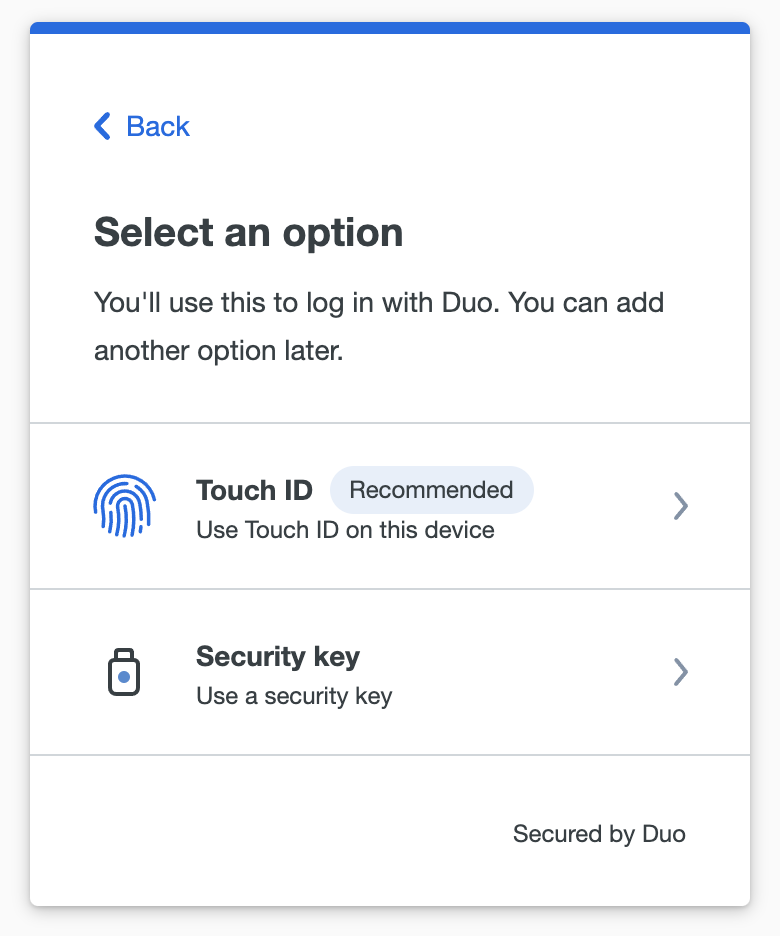
The options you see offered during Duo Passwordless setup depend on whether your organization allows use of platform authenticators (Touch ID, Windows Hello, etc.), roaming authenticators (security keys), or both.
Duo Push for passwordless login isn't shown as an option to choose during setup, and is instead automatically registered for you if your organization allows it and you used Duo Push to complete two-factor authentication when logging in to this application.
In this example the policy allows platform, roaming, and Duo Push authenticators. The user is accessing the application with Chrome on a MacBook, so the choices are to set up Touch ID or a security key.
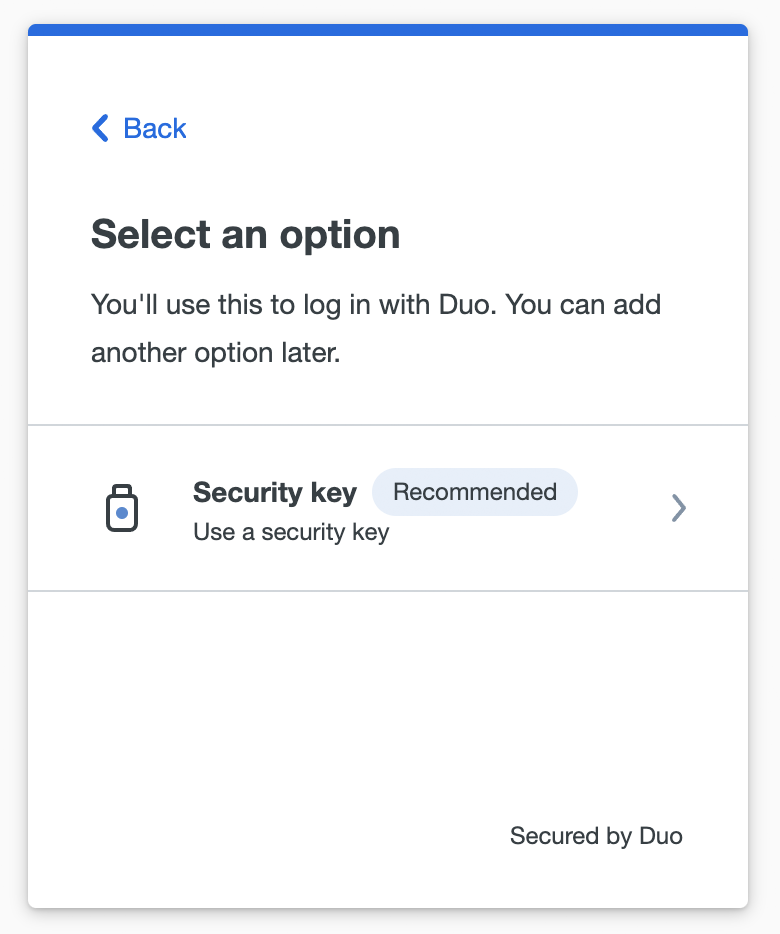
In this example, the organization allows roaming authenticators but not platform authenticators, so the only option is to set up a security key.
Note that if your organization allows both platform and roaming authenticators but your access device doesn't have a supported platform authenticator you'll only see the security key option at setup as well.
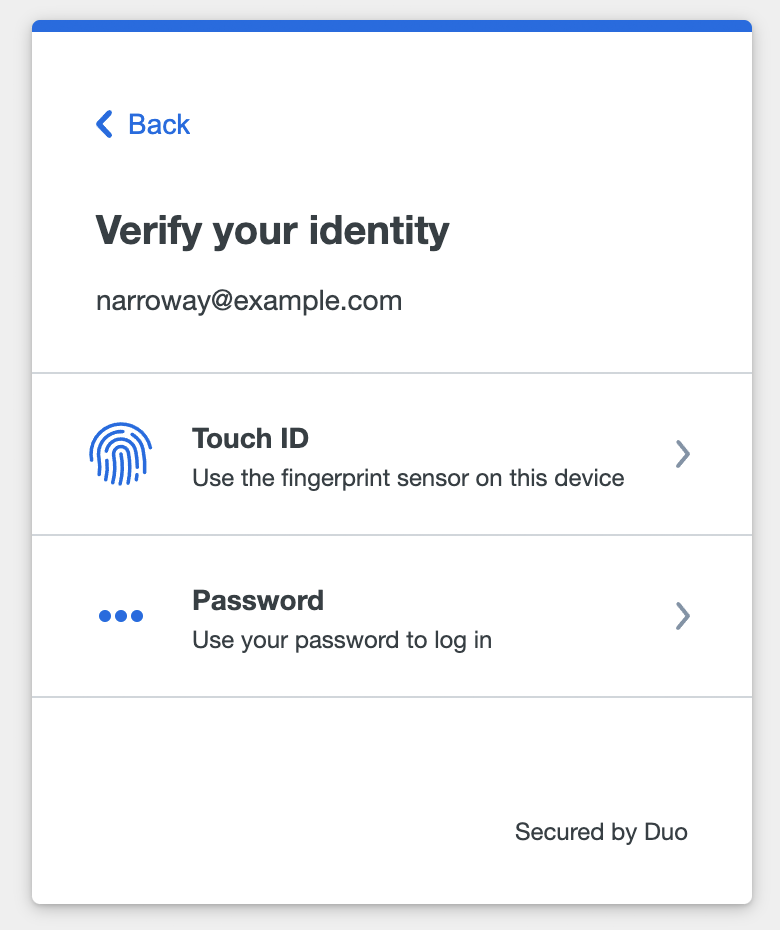
Duo Passwordless Login Options
Learn how to perform interactive passwordless registration or how to log in with these Duo Passwordless identity verification methods.
- Touch ID on a Mac
- Face ID/Touch ID on an iPhone or iPad
- Passkey
- Windows Hello
- Android Biometrics
- Security Key
- Duo Push
Touch ID on a Mac
In order to use Touch ID on macOS with Duo Passwordless, make sure you have the following:
- A Mac computer with a Touch ID button.
- A fingerprint enrolled in Touch ID (learn how to set up Touch ID on Mac at the Apple Support site).
- A recent version of Google Chrome or Safari. Other browsers on macOS are not supported.
- iCloud Keychain sync enabled on all the Apple devices you will use with Duo and the passkey you will create during setup.
Set up Touch ID
- Log into the Duo SSO application with your password and complete Duo authentication.
- Click Continue to begin setting up passwordless login.
- Click the Touch ID option to begin adding it to Duo.

- Read the Touch ID information and click Continue.
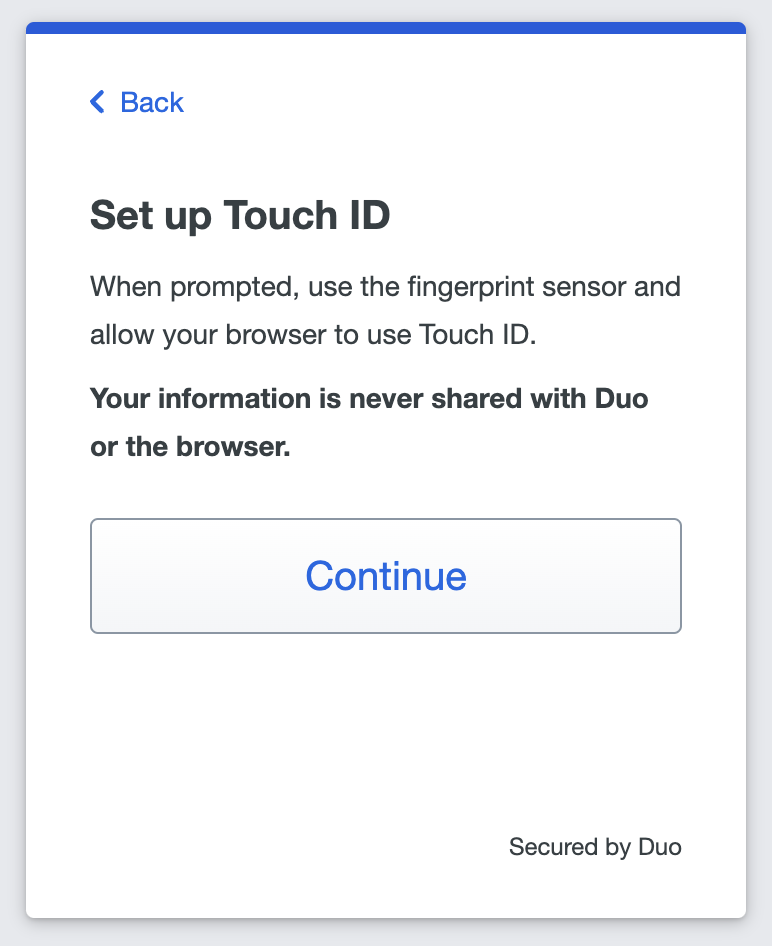
- The browser prompts you to verify your identity on duosecurity.com when adding Touch ID (Chrome example shown).
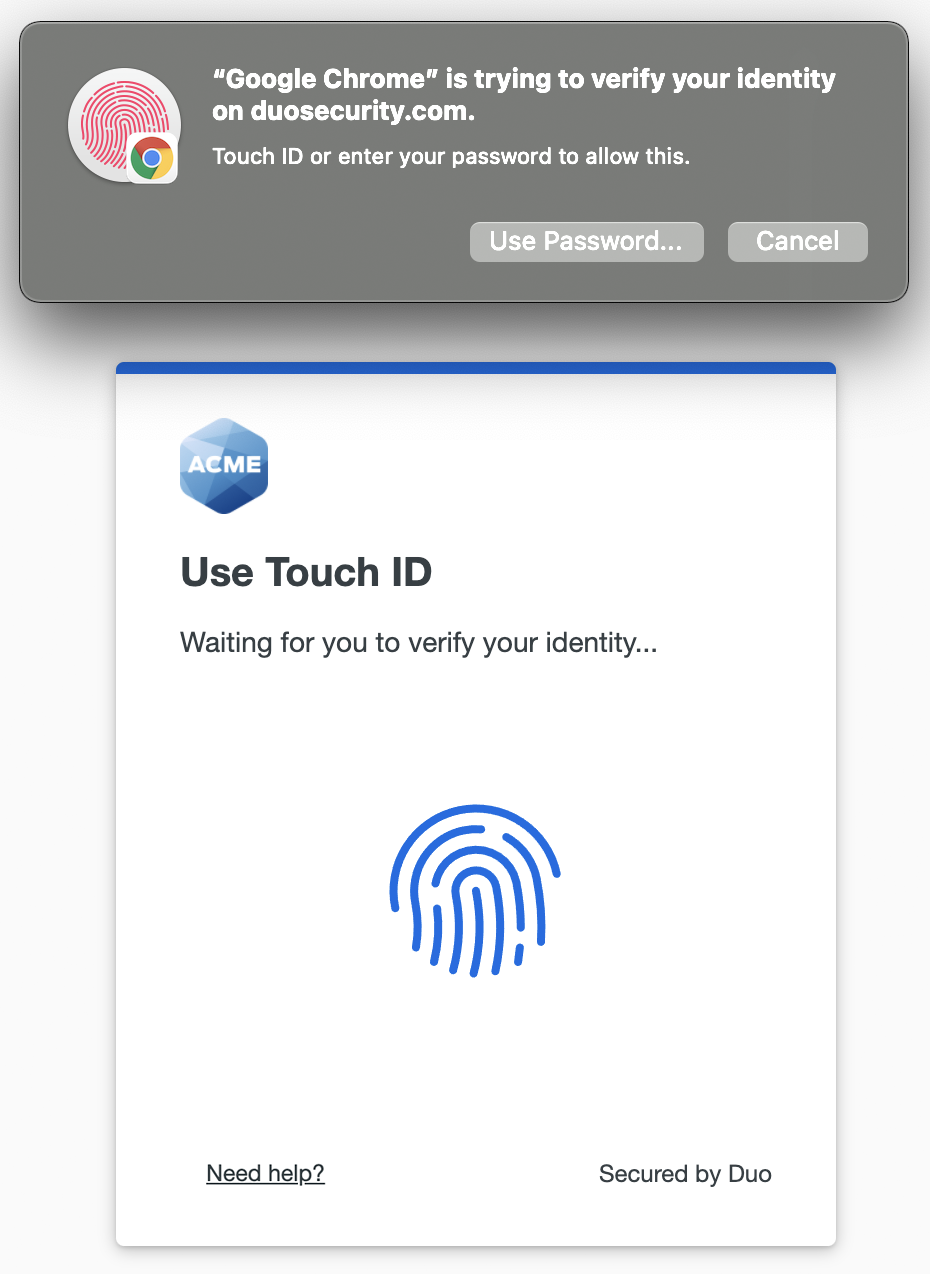
You may be prompted to enter your system password instead of tapping Touch ID if you haven't added your fingerprint to Touch ID on your Mac yet, or if you have your laptop closed so you can't access the Touch ID button. You can also choose to enter your system password. - Place your finger on the Touch ID button in the Touch Bar (or enter your system password) to complete Touch ID enrollment (Chrome example shown).

- When you receive confirmation that you added Touch ID as a verification method, tap Continue.
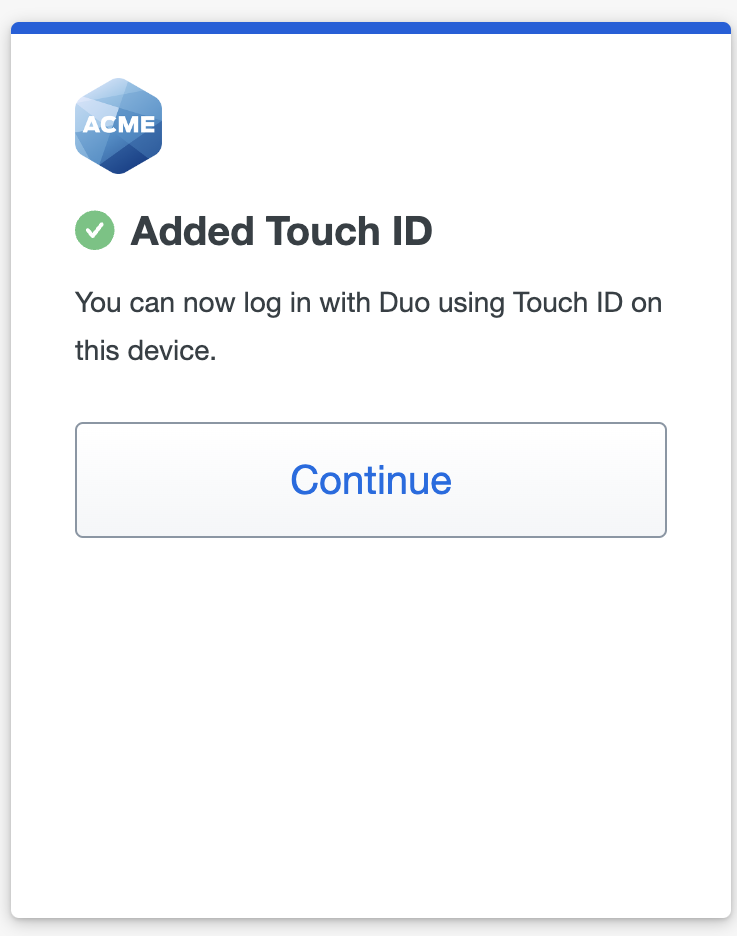
- You've added Touch ID as your passwordless login method. Click Done.
After completing Duo Passwordless setup you proceed to your application as a logged-in user.
Log in with Touch ID
The next time you log into this Duo SSO application from the Mac computer where you set up Touch ID for passwordless login, you'll enter your username and then — instead of entering your password — you can choose Touch ID to verify your identity.
Place your finger on the Touch ID button in the Touch Bar to complete logging in to the application, as you did when you set up Touch ID in Duo.

Successful Touch ID verification logs you in without entering a password, and Duo SSO sends you to the application as a logged in user.
Face ID or Touch ID on an iPhone or iPad
In order to use Face ID or Touch ID on an iPhone or iPad with Duo Passwordless, make sure you have the following:
- An iPhone or iPad that supports Face ID or Touch ID.
- Face ID or Touch ID already set up on the iPhone or iPad. Learn how to set up Face ID or set up Touch ID at the Apple Support site.
- iCloud Keychain sync enabled on all the Apple devices you will use with Duo and the passkey you will create during setup.
Depending on the option your device supports, you'll either scan your face to use Face ID during setup and while logging in, or you'll scan your fingerprint instead to use Touch ID.
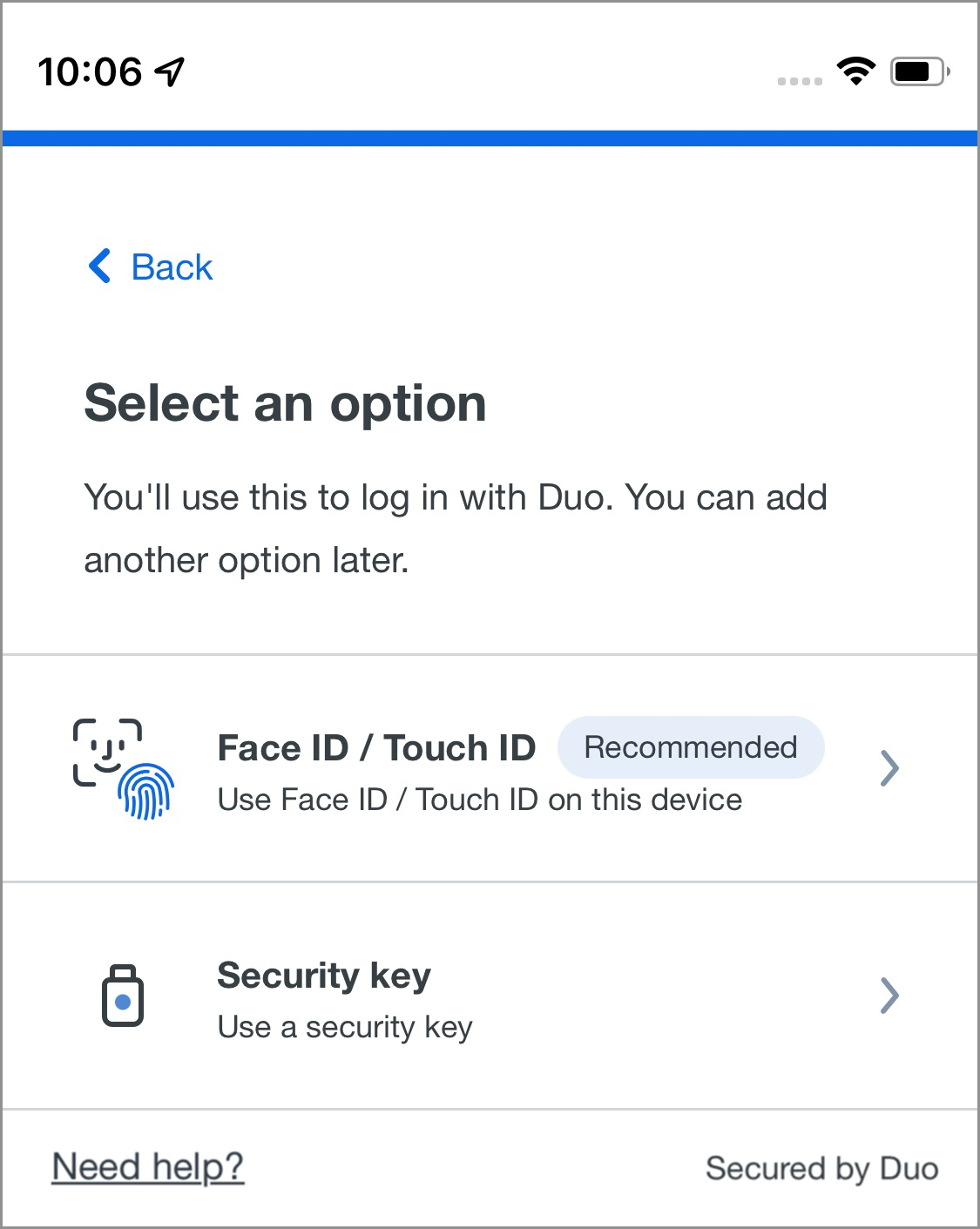
Set up Face ID/Touch ID
- Log into the Duo SSO application with your password and complete Duo authentication.
- Tap Continue to begin setting up passwordless login.
- Tap the Face ID/Touch ID option to begin adding it to Duo.
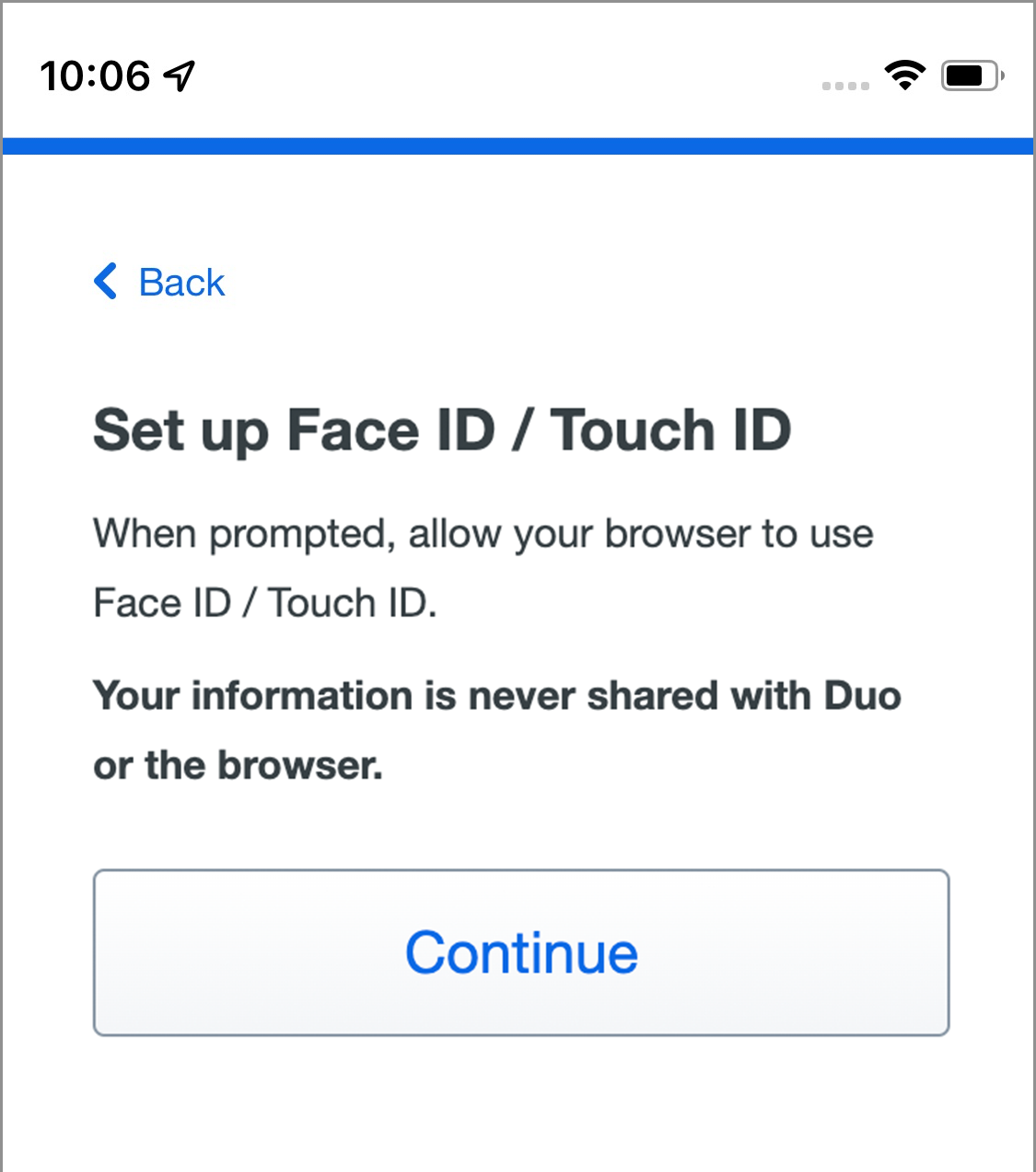
- Read the Face ID (or Touch ID) information and tap Continue.
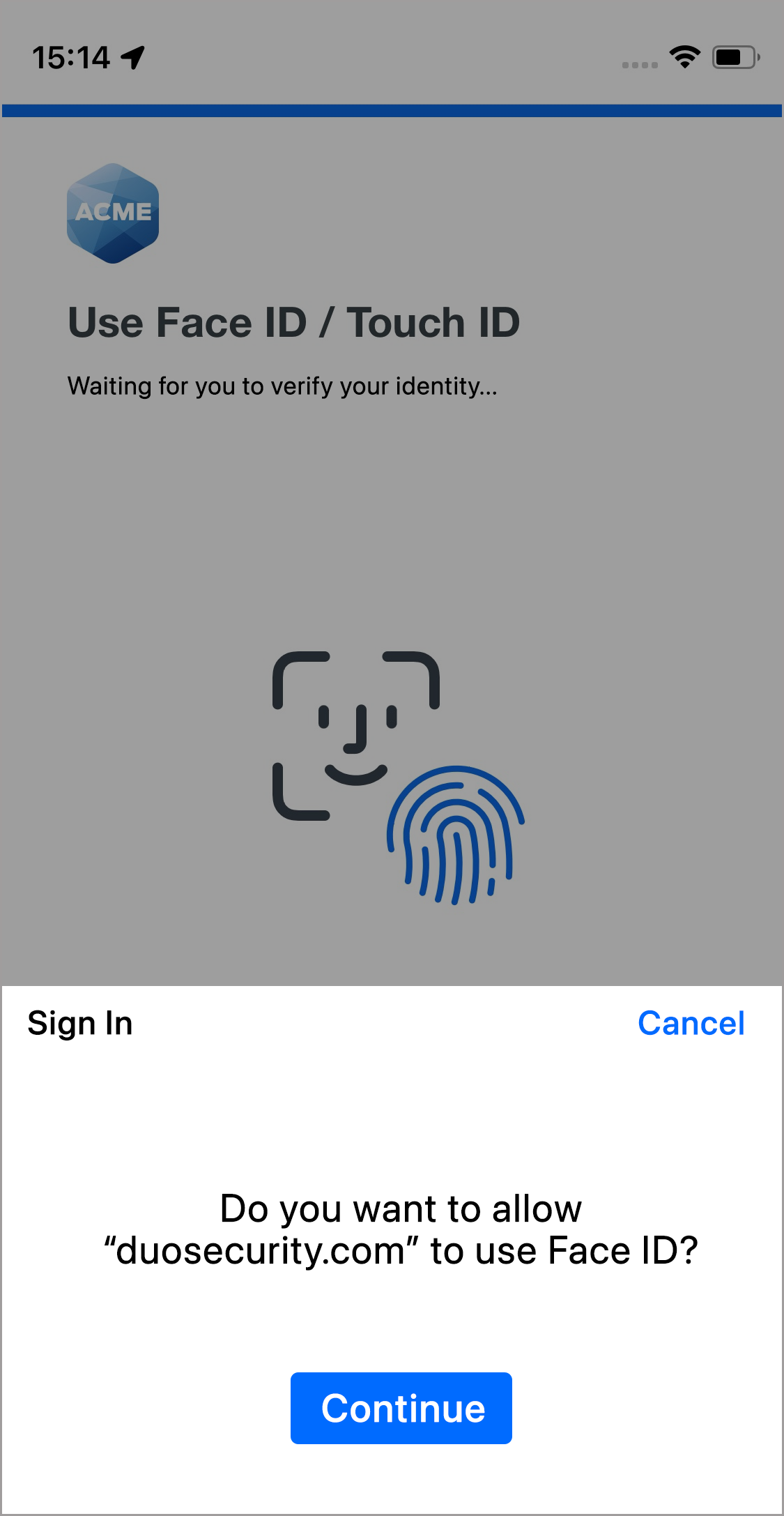
- Follow your device's instructions for scanning your face to complete Face ID verification or scan your fingerprint for Touch ID verification.
- When you receive confirmation that you added Face ID as a verification method click Continue.
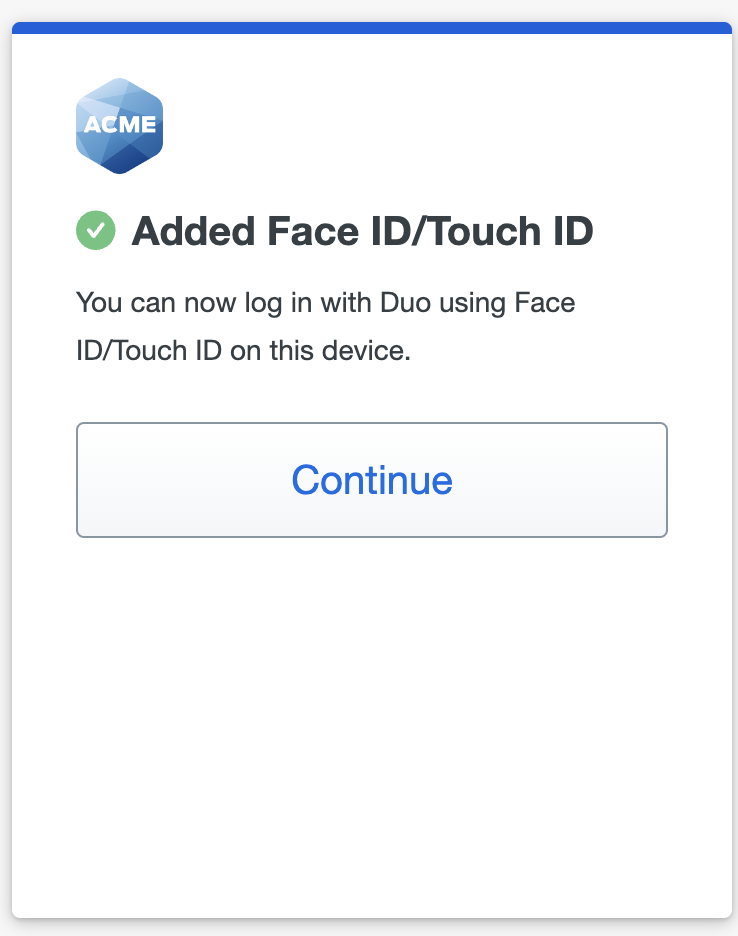
- You've added Face ID or Touch ID as your passwordless login method. Tap Done.
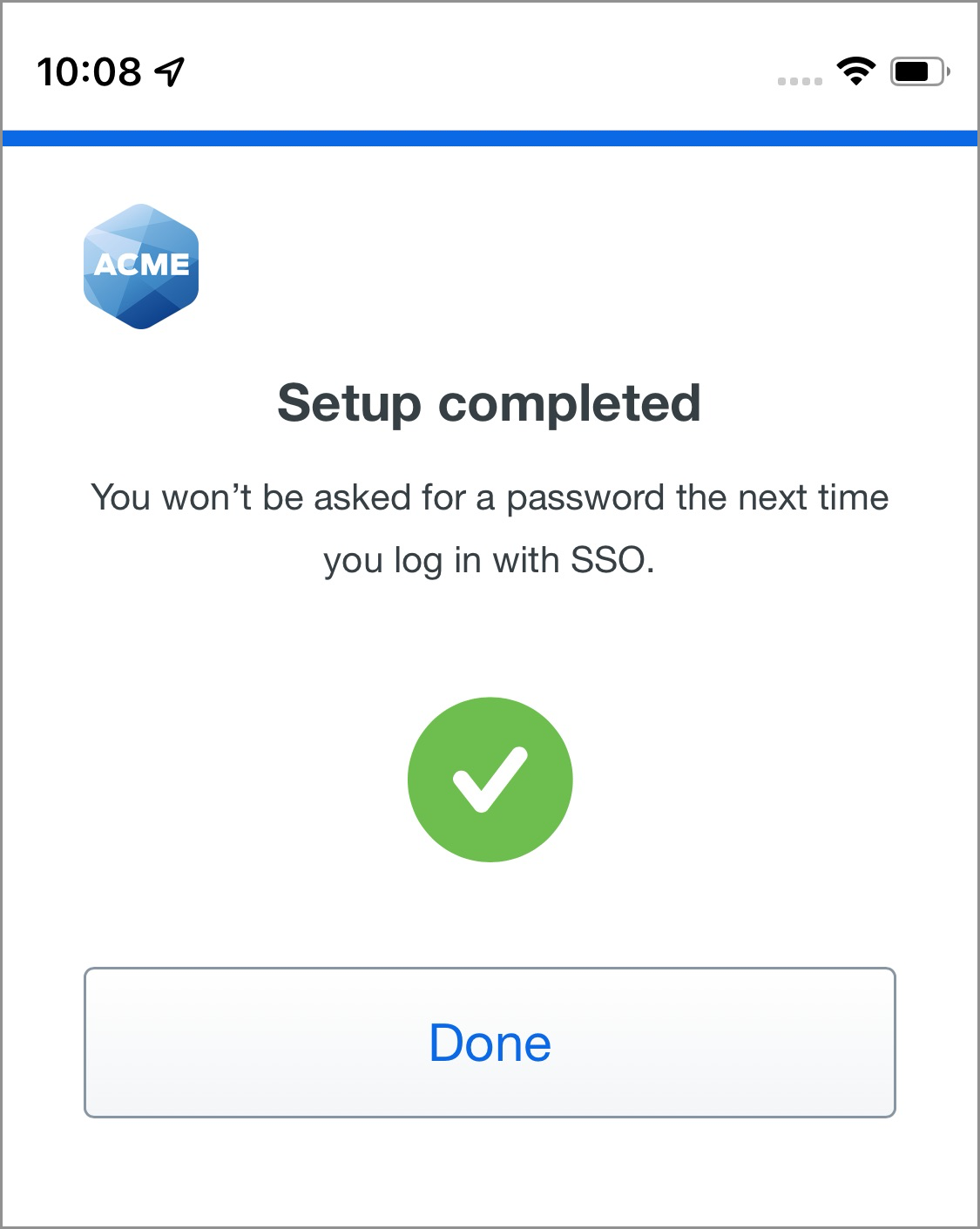
After completing Duo Passwordless setup you proceed to your application as a logged-in user.
Log in with Face ID
The next time you log into this Duo SSO application from the iPhone or iPad where you set up Face ID/Touch ID for passwordless login, you'll enter your username and then instead of entering your password you can choose Face ID/Touch ID to verify your identity. Tap Log in.
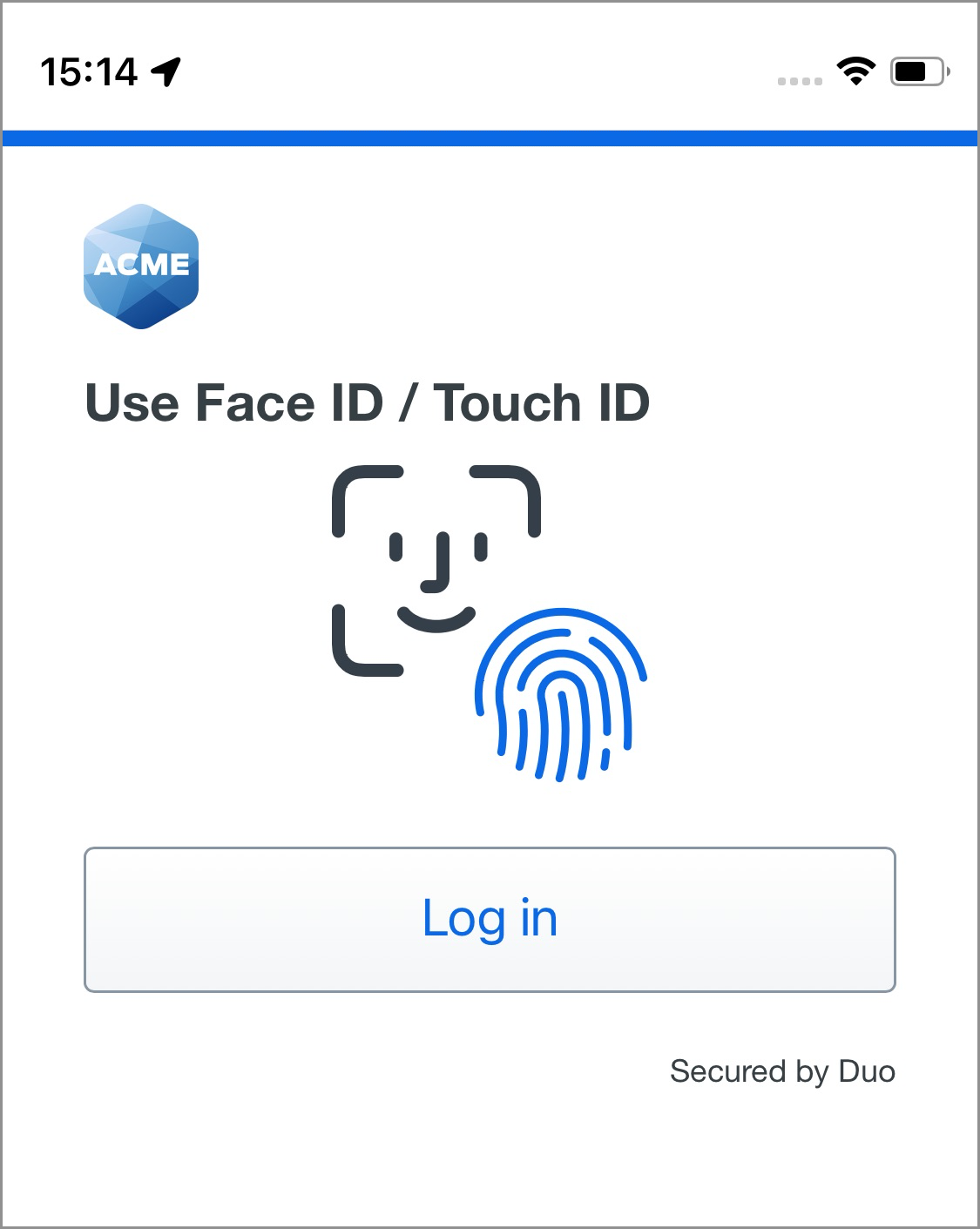
Follow your device's prompt to use Face ID or Touch ID, just like you did when you set up Face ID/Touch ID in Duo.

Successful Face ID/Touch ID verification logs you in without entering a password, and Duo SSO sends you to the application as a logged in user.
Passkeys
Passkeys with Apple Devices and Browsers
In order to use a passkey with Duo Passwordless, make sure you have at least two of the following devices:
- A Mac computer running macOS 13 or later and Safari.
- An iPhone running iOS 16 or later.
- An iPad running iPadOS 16 or later.
- iCloud Keychain sync enabled on all the Apple devices you will use with Duo and the passkey you will create during setup.
All devices must share the same iCloud account.
Set up a Passkey
First set up Touch ID on your Mac or Face ID or Touch ID on your iPhone or iPad.
Once you have set up one of your Apple devices, any other Mac computer (running macOS 13 or later), iPhone (running iOS 16 or later), or iPad (running iPadOS 16 or later) can be used to authenticate as long as they share an iCloud account.
Log in with a Passkey
The next time you log into this Duo SSO application from a Mac computer, iPhone or iPad where you share an iCloud account with the device you set up Face ID/Touch ID for passwordless login, you'll enter your username and then instead of entering your password you can choose Face ID/Touch ID to verify your identity. Tap Log in.
Follow your device's prompt to use Face ID or Touch ID, just like you did when you set up Face ID/Touch ID in Duo.
Successful Face ID/Touch ID verification logs you in without entering a password, and Duo SSO sends you to the application as a logged in user.
Windows Hello
In order to use Windows Hello with Duo Passwordless, make sure you have the following:
- A device running Windows 10 or later.
- Windows Hello set up on the device for signing in with a PIN, fingerprint, or facial recognition. Learn how to set up Windows Hello at the Microsoft support site.
- A supported browser: Chrome, Edge, or Firefox. Refer to the Duo Passwordless browser support table. Note that Chrome Incognito and Edge InPrivate browsing won't work with Windows Hello, but will work with Security Keys.
Set up Windows Hello
- Log into the Duo SSO application with your password and complete Duo authentication.
- Click or tap Continue to begin setting up passwordless login.
- Click or tap the Windows Hello option to begin adding it to Duo.
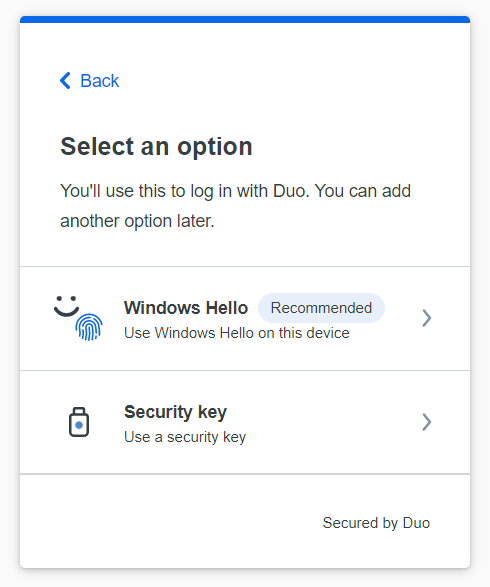
- Read the Windows Hello information and click or tap Continue.
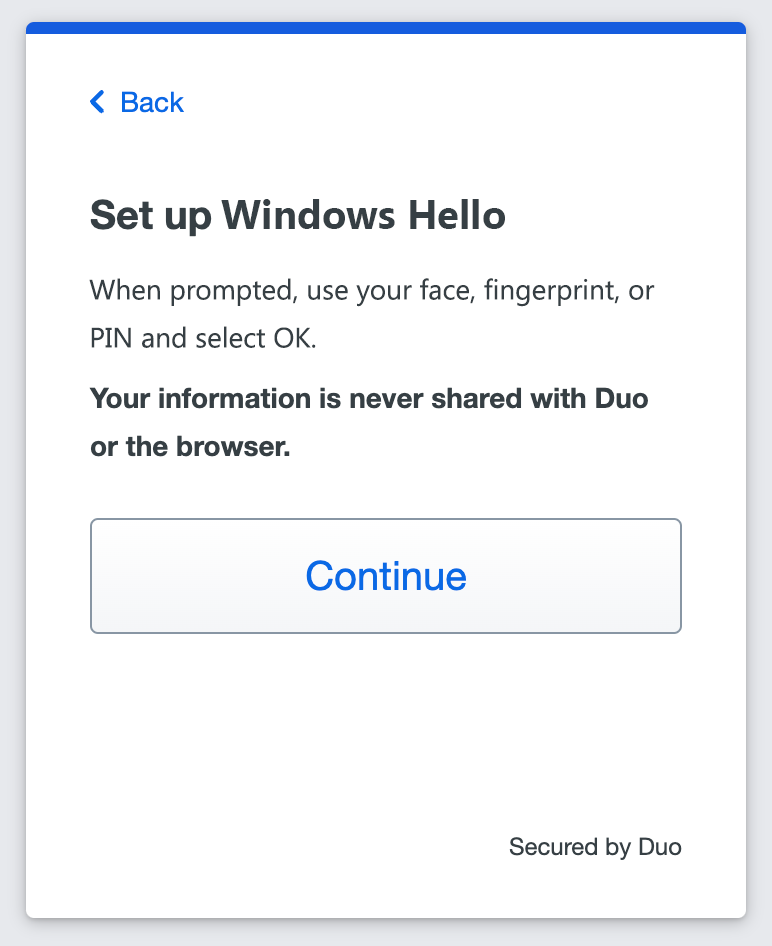
- Follow the Windows Hello instructions to verify your identity by entering your PIN, scanning your fingerprint, or pointing your face to your camera.
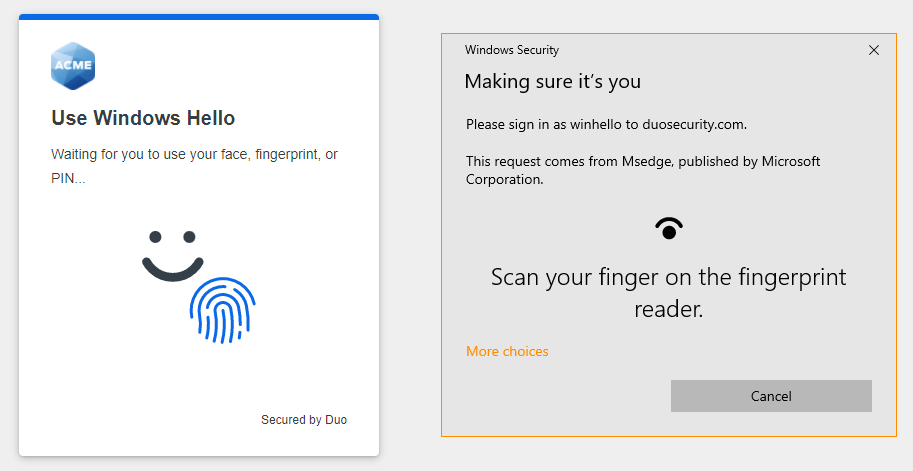
- When you receive confirmation that you added Windows Hello as a verification method click or tap Continue.
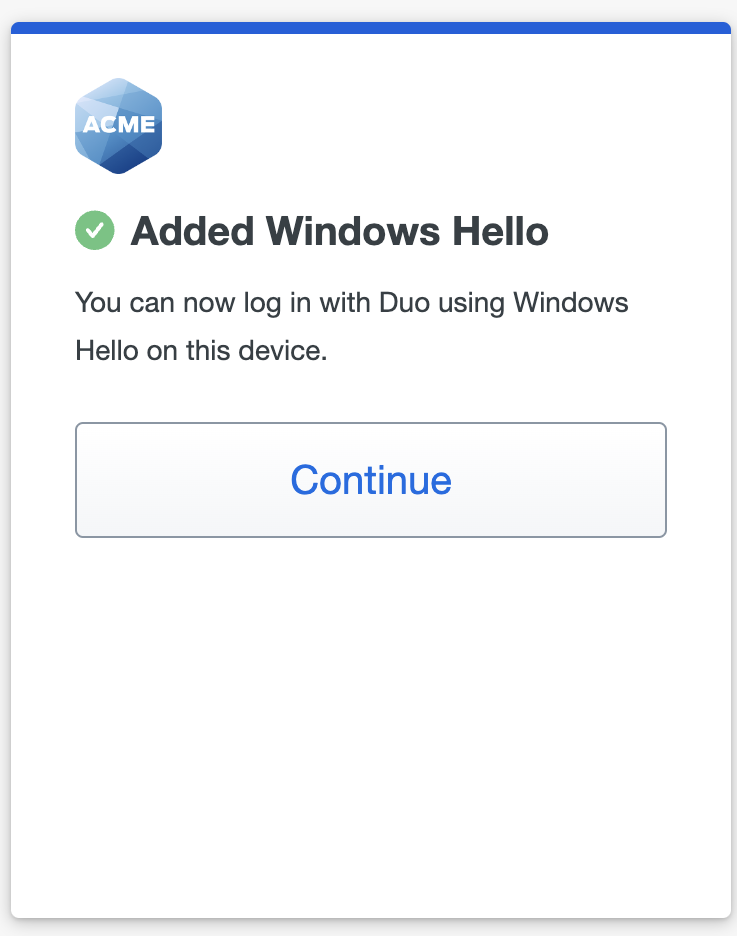
- You've added Windows Hello as your passwordless login method. Tap Done.
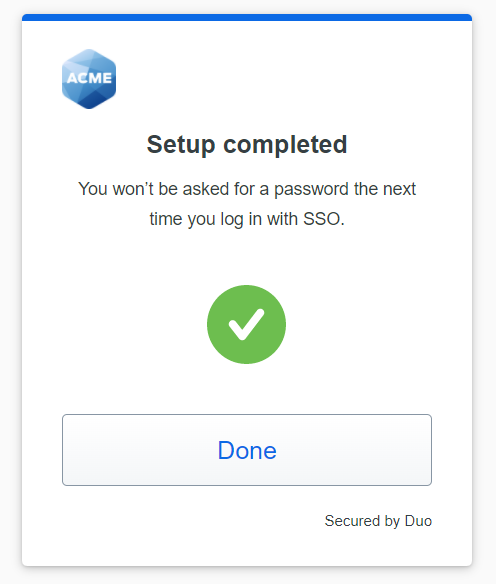
After completing Duo Passwordless setup you proceed to your application as a logged-in user.
Log in with Windows Hello
The next time you log into this Duo SSO application from the Windows system where you set up Windows Hello for passwordless login, you'll enter your username and then instead of entering your password you can choose Windows Hello to verify your identity. Click or tap Log in.
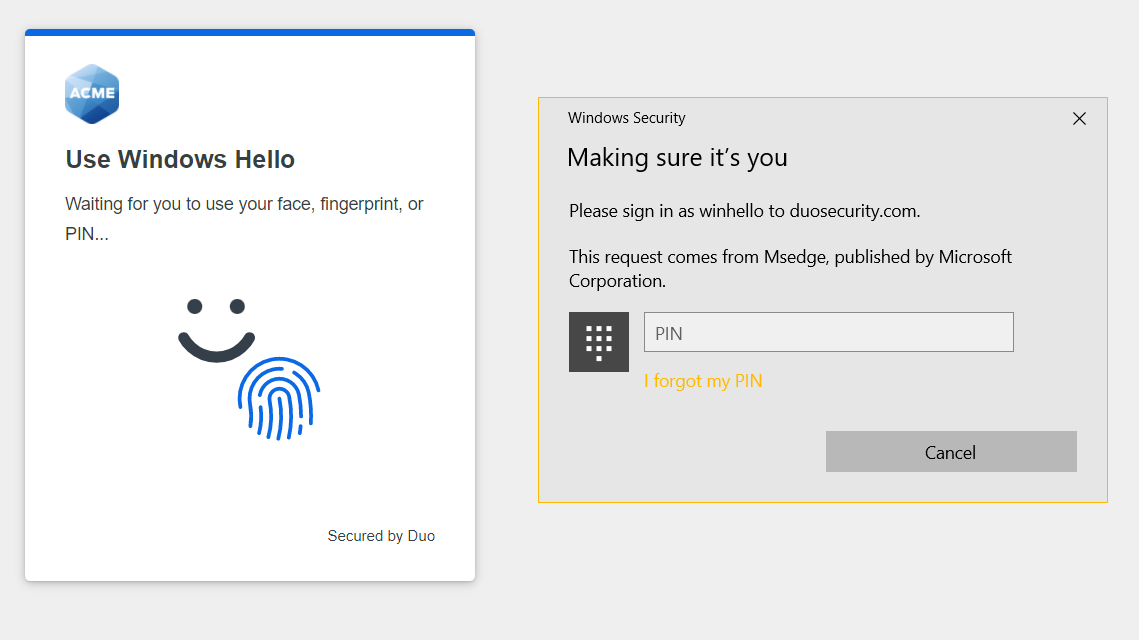
Follow your device's prompt to enter your Windows Hello PIN, scan your fingerprint, or use facial recognition, just like you did when you set up Windows Hello in Duo.
Successful Windows Hello verification logs you in without entering a password, and Duo SSO sends you to the application as a logged in user.
Android Biometrics
In order to use Android Biometrics with Duo Passwordless, make sure you have the following:
- An Android device that supports biometrics, like fingerprint or face unlock.
- Facial or fingerprint unlock set up on that device. Go to Settings → Security to change your unlock settings. Refer to the Google support articles Unlock your Pixel phone with your fingerprint and Unlock your Pixel phone with your face, the Samsung articles Set up and use the fingerprint sensor on your Galaxy phone and Use Facial recognition security on your Galaxy phone, or your device manufacturer's support site for examples of how to do this.
Set up Android Biometrics
- Log into the Duo SSO application with your password and complete Duo authentication.
- Tap Continue to begin setting up passwordless login.
- Tap the Device verification option to begin adding it to Duo.
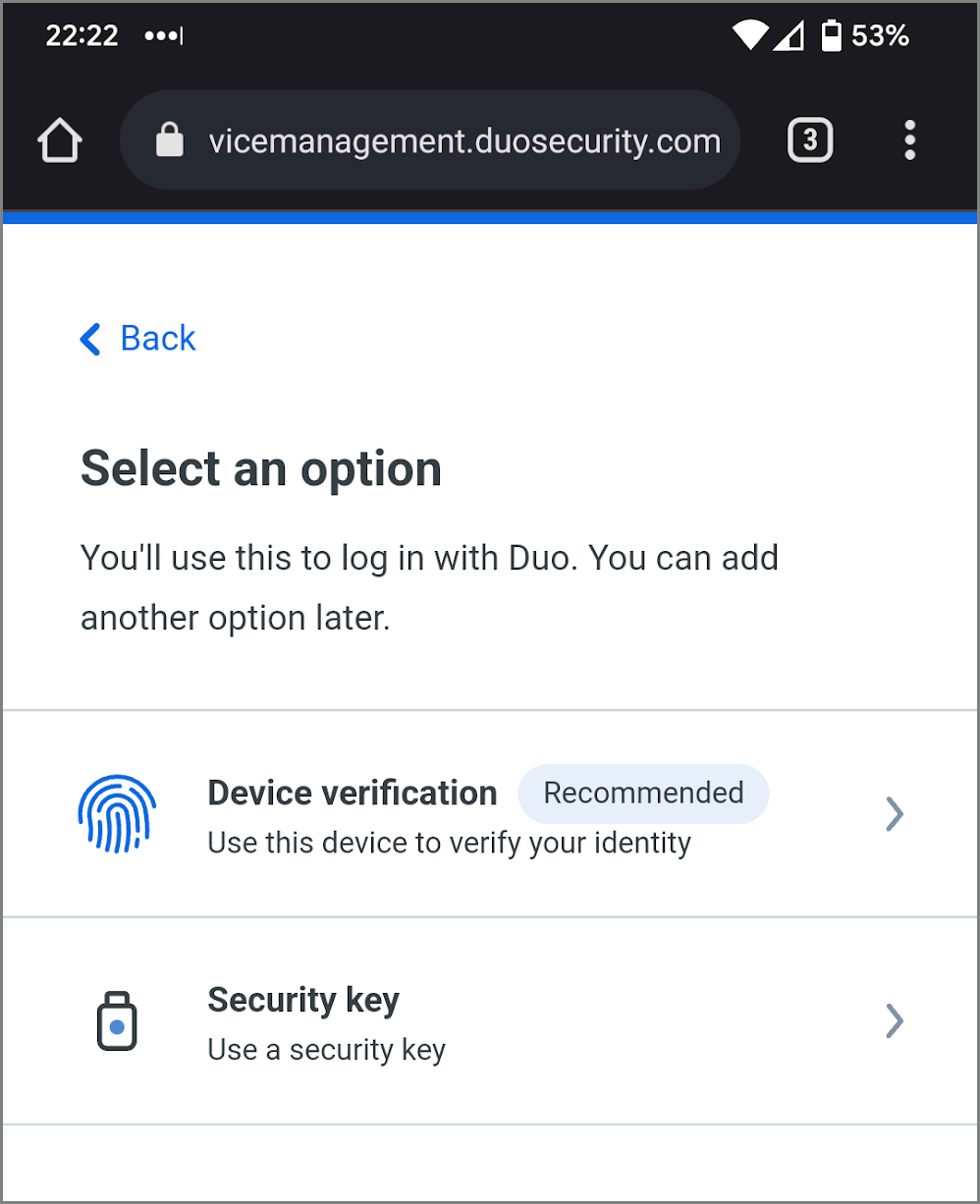
- Read the device verification information and click or tap Continue.
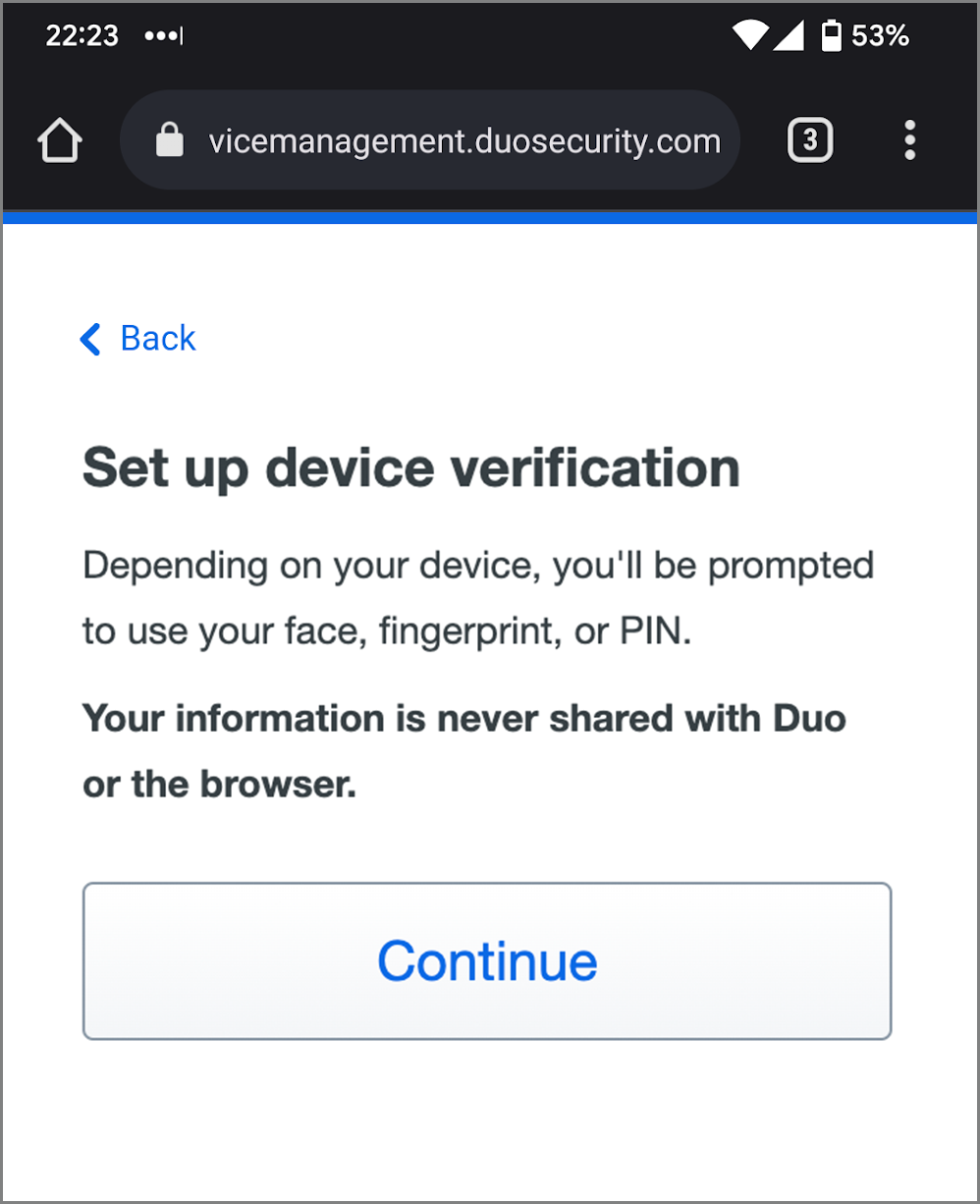
- Follow the Android instructions to verify your identity by scanning your fingerprint or pointing your face to your camera. If you aren't able to do either of those biometric checks, you can enter your Android PIN.
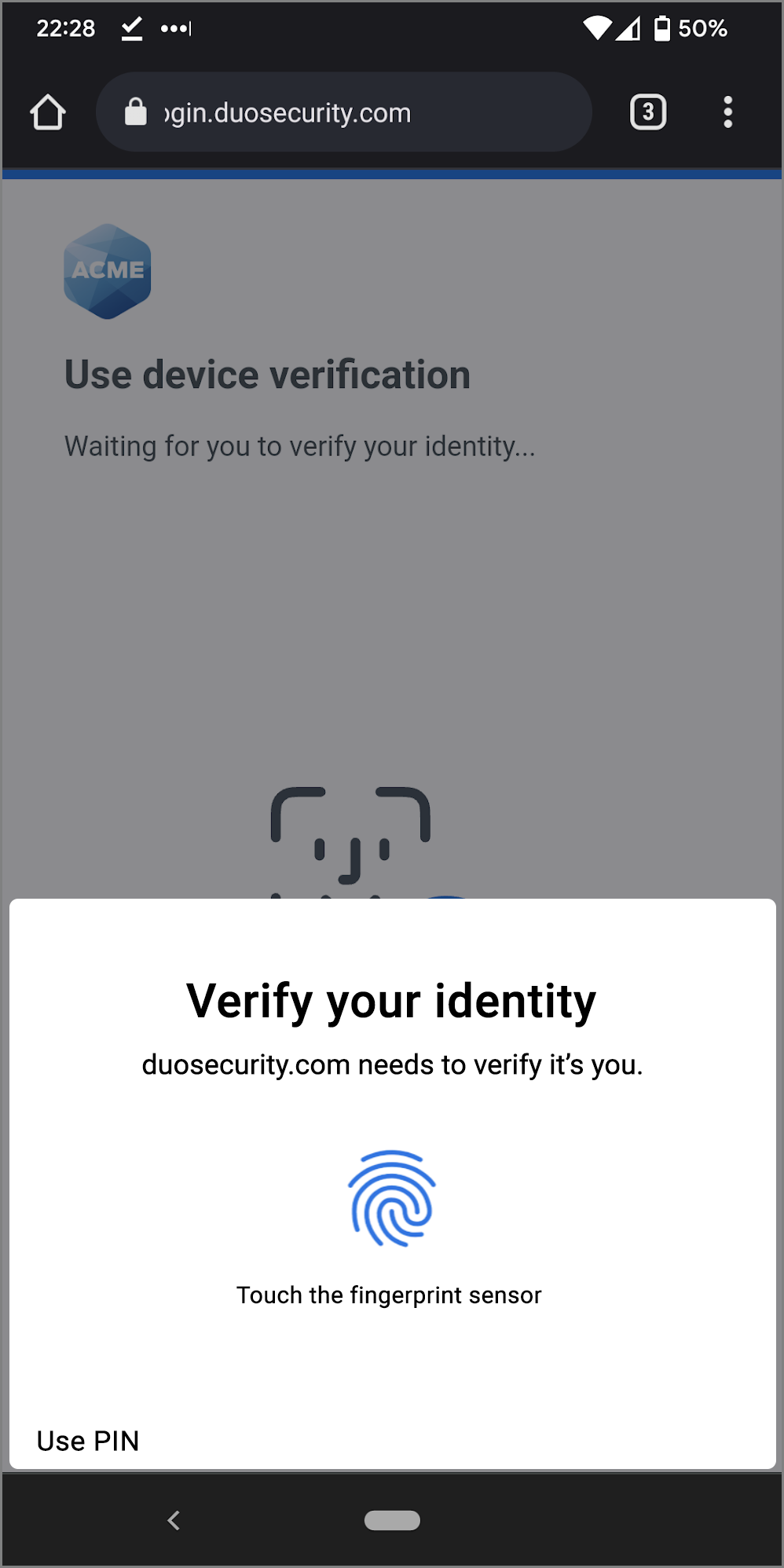
- When you receive confirmation that you added your Android device as a verification method tap Continue.
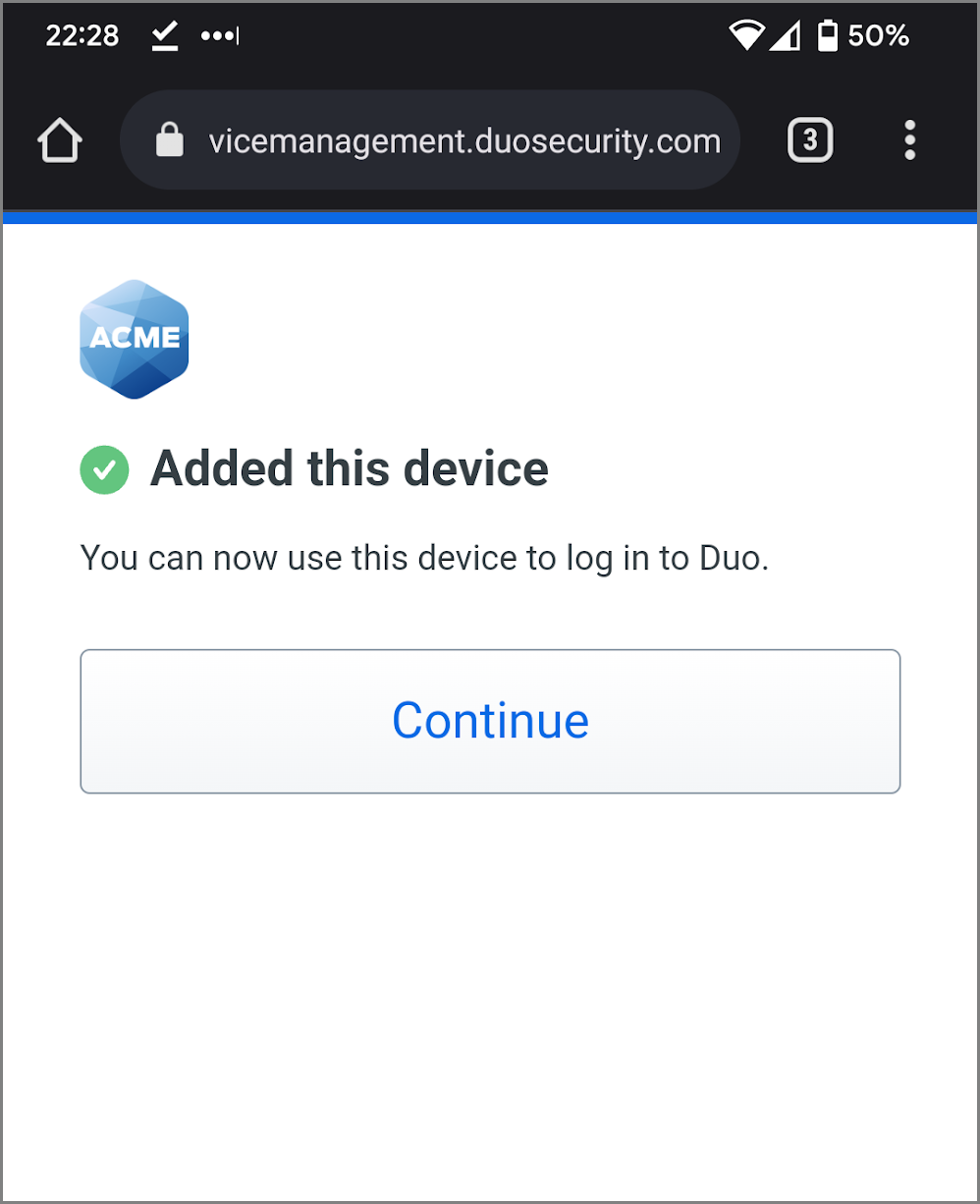
- You've added Android biometric device verification as your passwordless login method. Tap Done.
After completing Duo Passwordless setup you proceed to your application as a logged-in user.
Log in with Android Biometrics
The next time you log into this Duo SSO application from the Android device where you set up biometric device verification for passwordless login, you'll enter your username and then instead of entering your password you can choose device verification to verify your identity. Tap Log in.
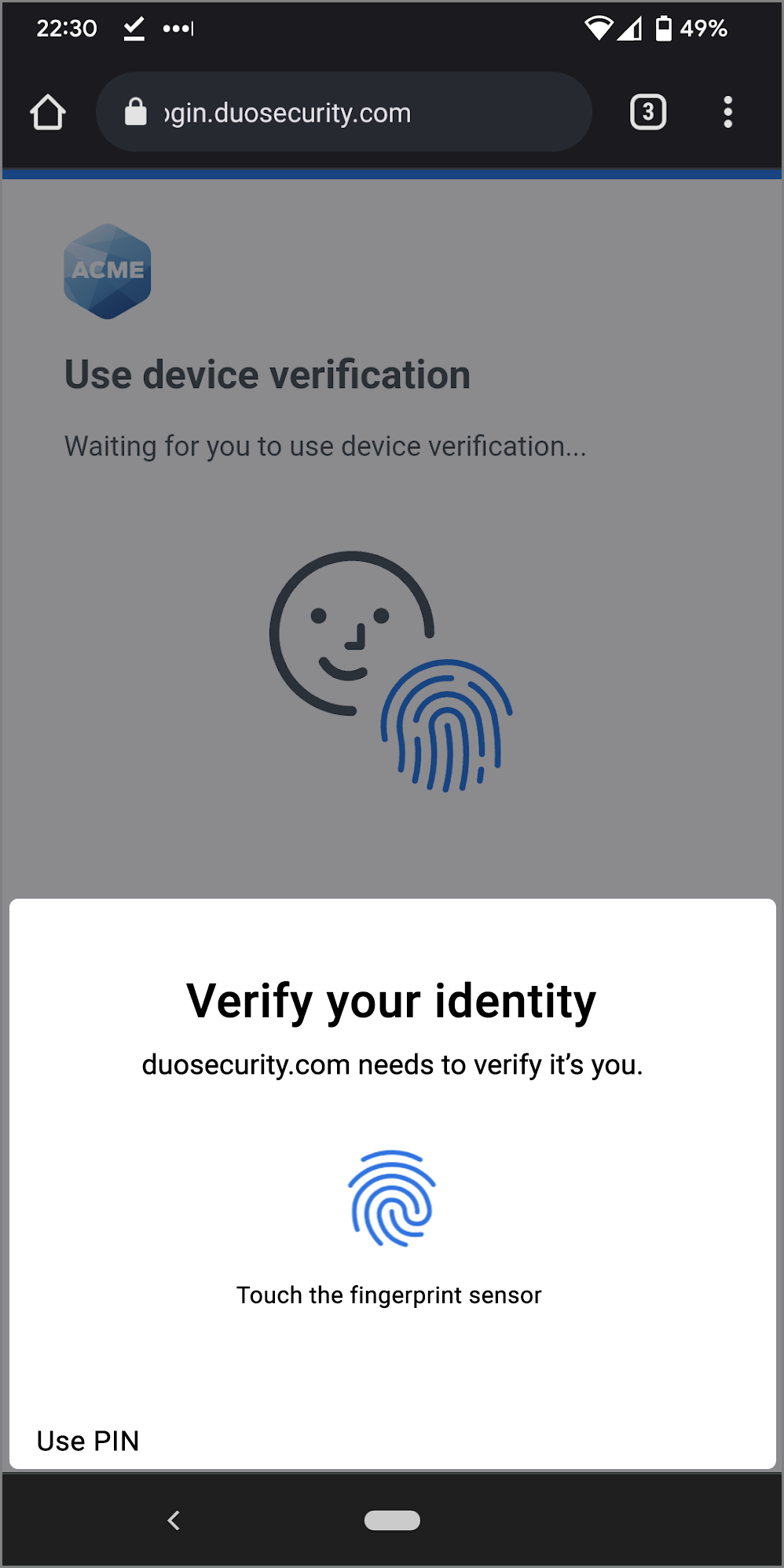
Follow your device's prompt to scan your fingerprint or use facial recognition, just like you did when you set up your Android device in Duo.
Successful Android device verification logs you in without entering a password, and Duo SSO sends you to the application as a logged in user.
Security Keys
A security key is an external device that sends a signed response when tapped or pressed back to Duo to validate your login. Duo uses the WebAuthn authentication standard to interact with your security keys. You may also see WebAuthn referred to as "FIDO2".
Duo considers security keys to be roaming authenticators, meaning you can register your security key for passwordless on one computer, and then connect it to a different computer to use it for passwordless login for the same account. You could set up Duo Passwordless with a USB security key on your MacBook, and then plug that same USB security key into a Windows computer to log in to a Duo SSO application without typing your password.
To use a security key with Duo Passwordless, make sure you have the following:
- A supported security key. WebAuthn/FIDO2 security keys from Yubico or Feitian are good options.
- The security key must be a biometric key (i.e. a fingerprint reader), or must be configured with a PIN for FIDO2 use. Refer to your security key vendor's support information to learn how to configure a PIN for your security key, for example, this article from Yubico describes how to use and set PINs for YubiKey security keys.
- A supported browser: Chrome, Safari, Firefox (excluding macOS), or Edge. Refer to the Duo Passwordless browser support table.
Set up Security Keys
Make sure that your security key's PIN or biometric verification works before trying to set it up in Duo. If your security key doesn't meet the requirements, you will need to close your browser tab or window to exit the setup process and start your login attempt again.
- Connect your FIDO2 security key to the device you'll use to log into a Duo SSO application.
- Log into the Duo SSO application with your password and complete Duo authentication.
- Click or tap Continue to begin setting up passwordless login.
- Click or tap the Security key option to begin adding it to Duo. You'll only see this option offered if your Duo administrator allows use of roaming passwordless authenticators.

- Read the security key information and click Continue.
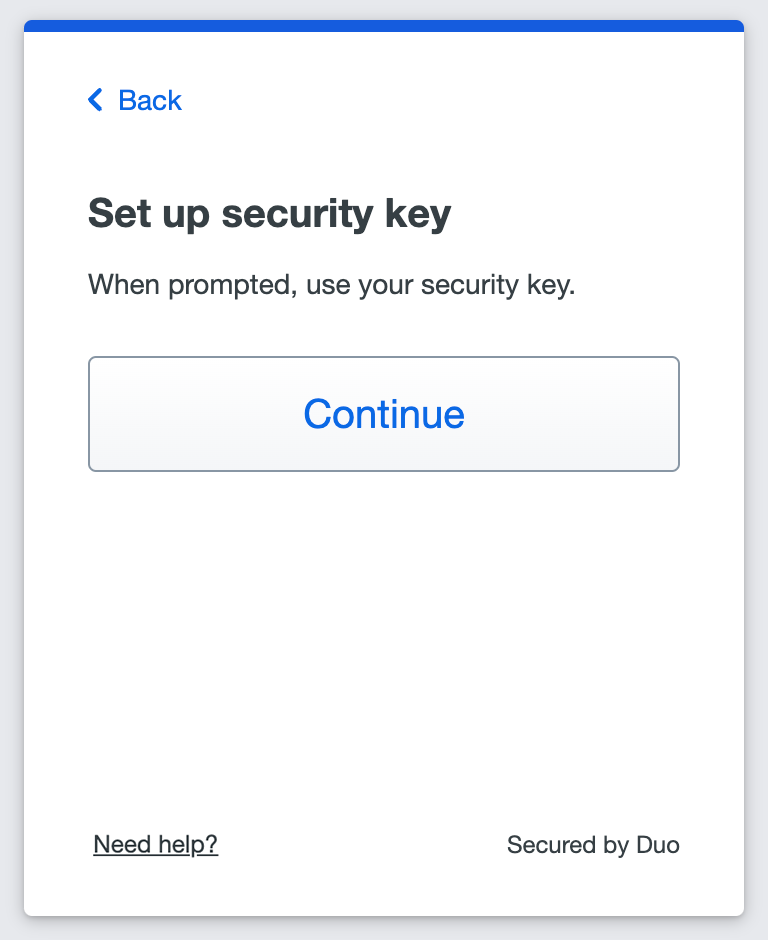
- Enter your security key's PIN or perform biometric verification when prompted (Chrome example shown).
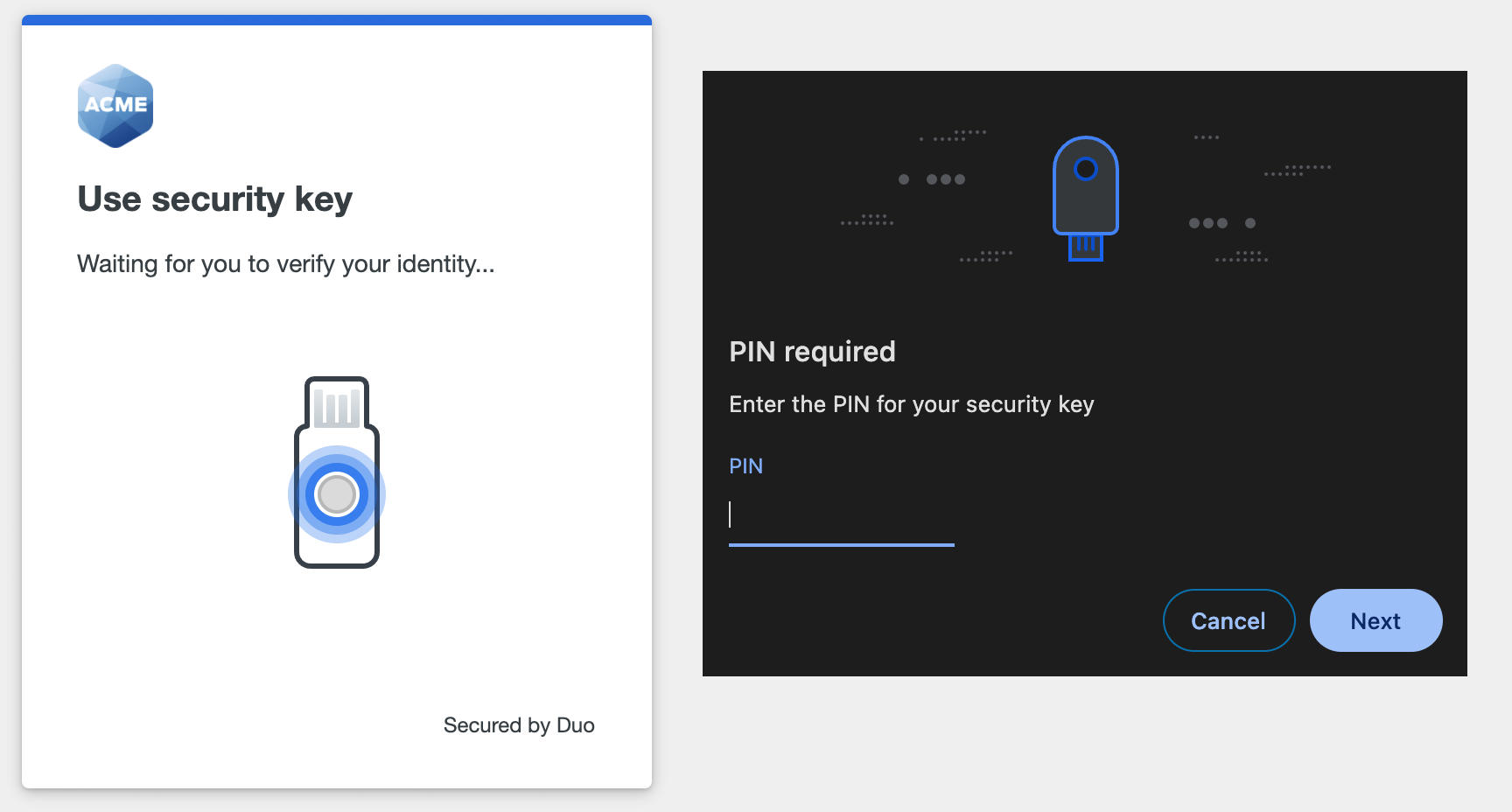
- Tap the security key to complete verification (Chrome example shown).
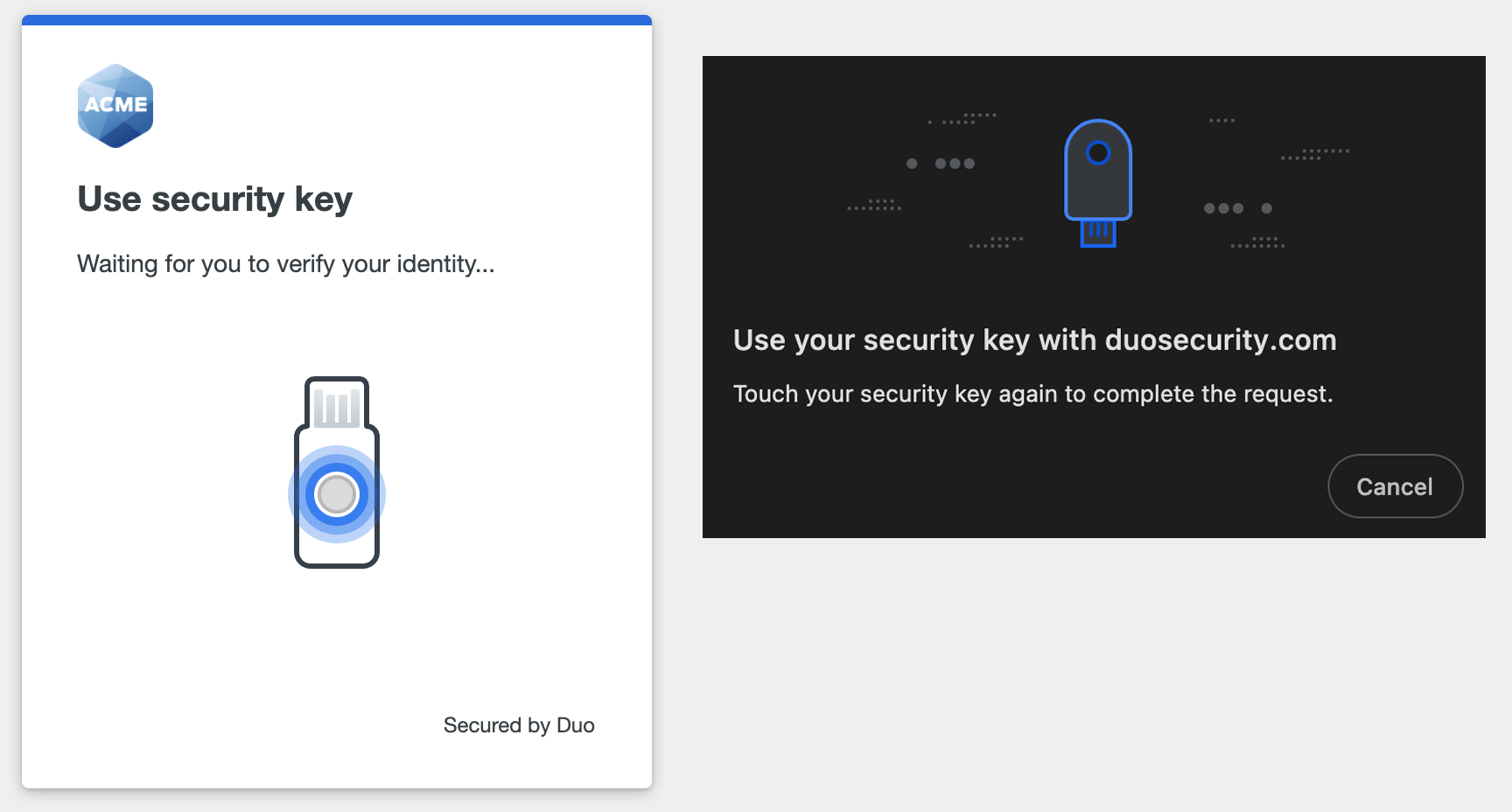
- When you receive confirmation that you added your security key as a verification method click or tap Continue.
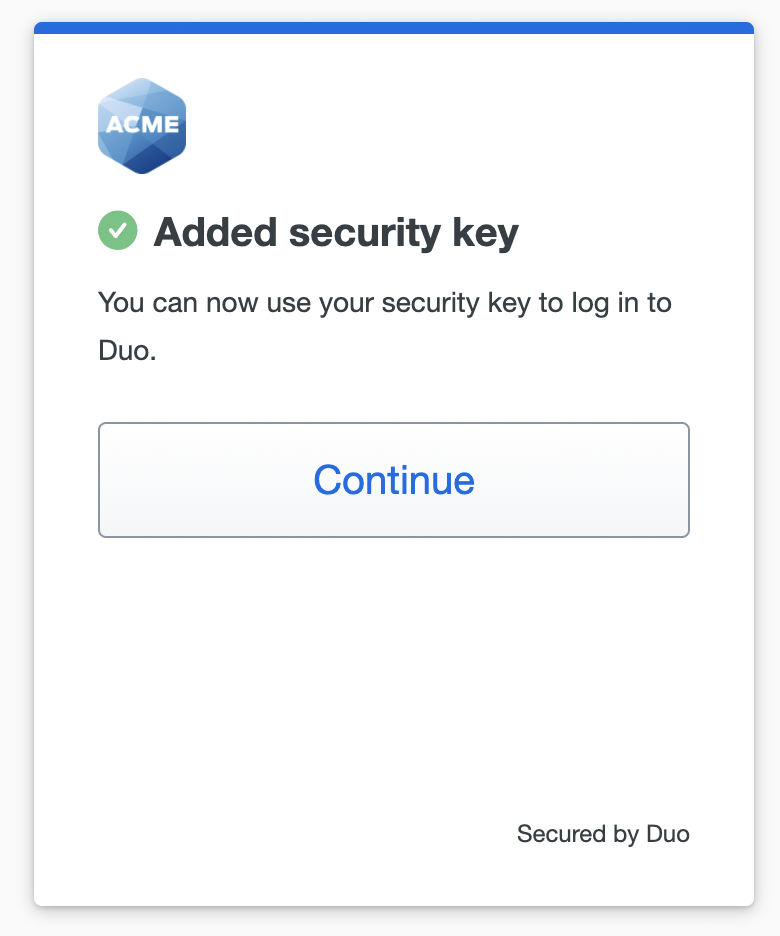
- You've added a security key as your passwordless login method. Click Done.

After completing Duo Passwordless setup you proceed to your application as a logged-in user.
Log in with Security Keys
The next time you log into this Duo SSO application — from the device where you set up your security key or another device where you connected that same security key — you'll enter your username and then instead of entering your password you can choose Security Keys to verify your identity.
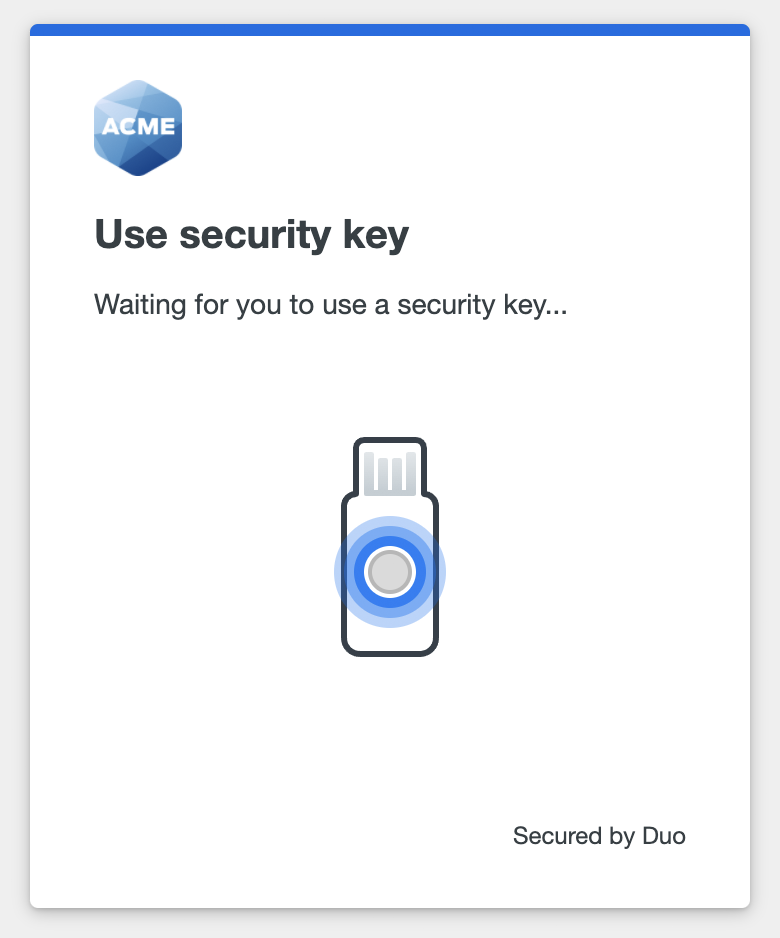
Enter your security key's PIN or let the security key scan your fingerprint, just like you did when you set up Security Keys in Duo (Windows Edge example shown).
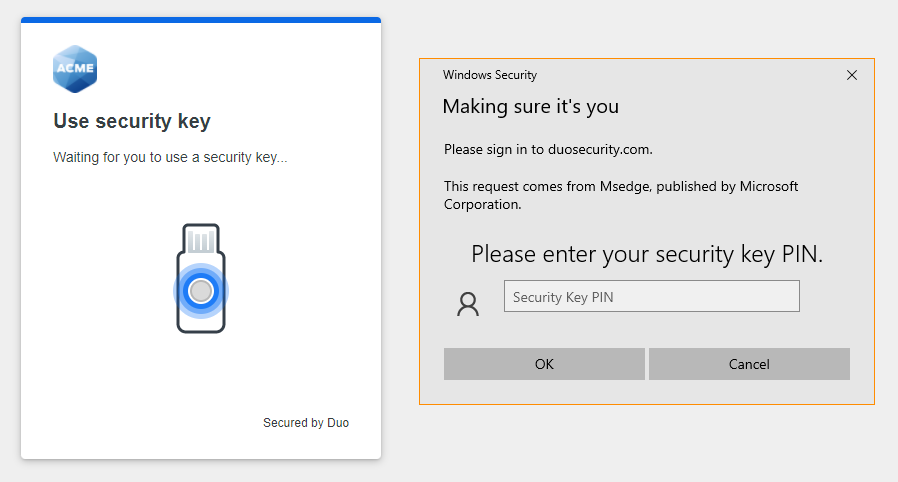
Then, when prompted, tap the security key again to complete your passwordless login (Windows Edge example shown).
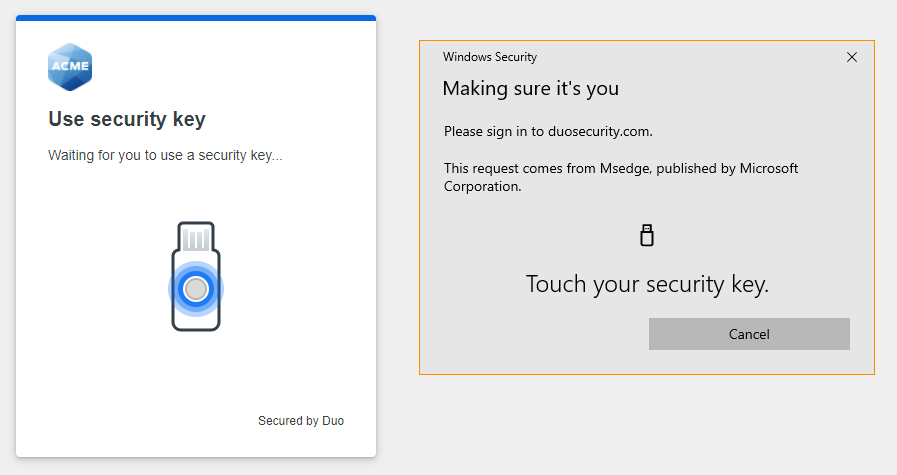
Successful security key verification logs you in without entering a password, and Duo SSO sends you to the application as a logged in user.
Duo Push
Complete Duo Passwordless login by approving a Duo Push request sent to your iOS or Android device.
If you previously activated Duo Mobile for two-factor authentication and have not set up a passwordless roaming or platform authenticator yet, then we can enable your existing Duo Push device for Duo Passwordless.
When you log into a Duo Single Sign-On application with your username and password and use Duo Push to perform Duo two-factor authentication, that will register your phone with Duo Mobile as a passwordless authenticator good for approving future logins from the same access device and browser.
Duo sets a “known device” browser cookie on the computer, phone, or tablet that you used to access the application with Duo Push. We then check for that browser cookie during your next login. If the cookie is still present, you can use Duo Passwordless to log in. If not, you will need to enter your username and password.
Set up Duo Push
There are no special registration steps you need to complete to use Duo Push with Duo Passwordless. It will happen automatically if you use Duo Push to approve a two-factor authentication request.
- Log into a Duo SSO application with your username and password.
- Use Duo Push to complete two-factor authentication. If the application doesn't automatically try to use Duo Push then you can cancel the request, click or tap Other options to see your list of Duo authentication methods, and select Duo Push from the list.
- After approving the Duo Push login request you proceed to your application as a logged-in user.
If you are a new user and have never enrolled in Duo before, you will enter the two-factor enrollment process during which you can set up Duo Push. After completing first-time enrollment, sign in to Duo SSO with your username, password, and Duo Push to then initiate the Duo Push passwordless registration.
The next time you log into Duo SSO from that same system, using the same browser as before, and enter your username, you will see a notification that tells you that you can use Duo Mobile to log in without a password.
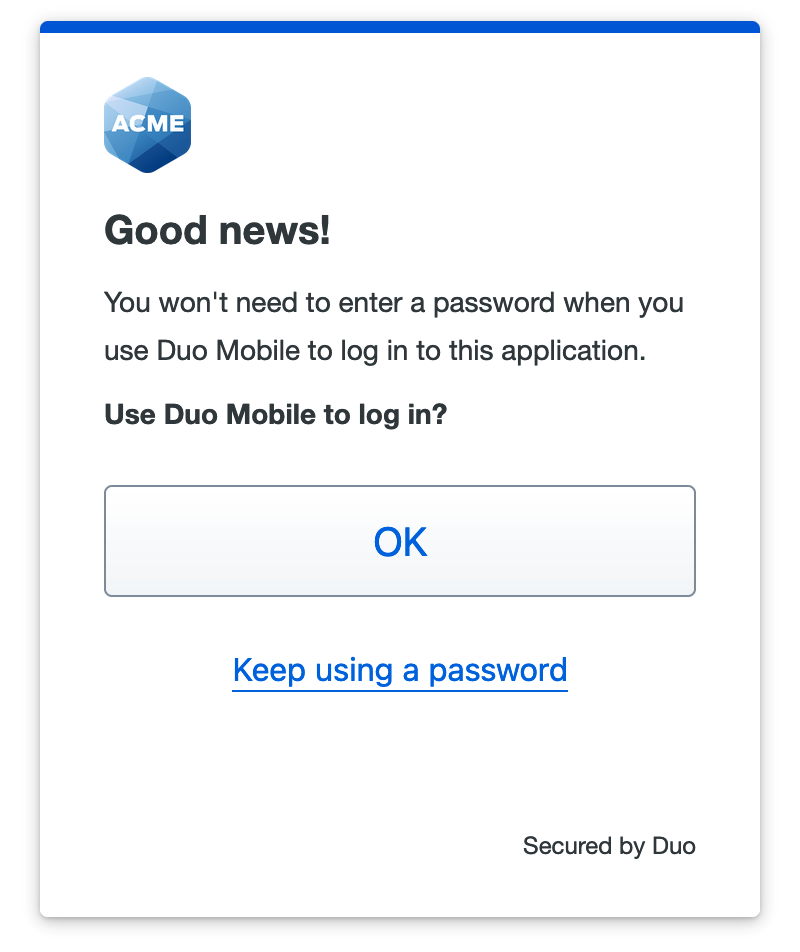
If your organization's Duo administrator has enabled platform or roaming authenticators for Duo Passwordless, then Passwordless login prefers one of those methods over Duo Push. So, if your access device has a WebAuthn platform authenticator available (like Touch ID), or if your device supports security keys, then you will see the beginning of the Duo Passwordless setup process.
After you complete platform or roaming passwordless authenticator registration then your existing Duo Push device is also enabled as a fallback authenticator for Duo Passwordless in that browser for that access device. However, you won't receive a message saying that you can now use Duo Mobile to log in to the application like a user without a platform or roaming passwordless authenticator sees.
Log in with Duo Push
If Duo Passwordless picks your registered platform or roaming authenticator and you want to use Duo Push instead, you can cancel the request in progress and click or tap Show other options to select Duo Push for this passwordless application login.
When you opt to use Duo Push for passwordless login for the first time you will be shown a six-digit verification code in the Duo browser prompt. Enter this code into the Duo Mobile login request on your Android or iOS device.
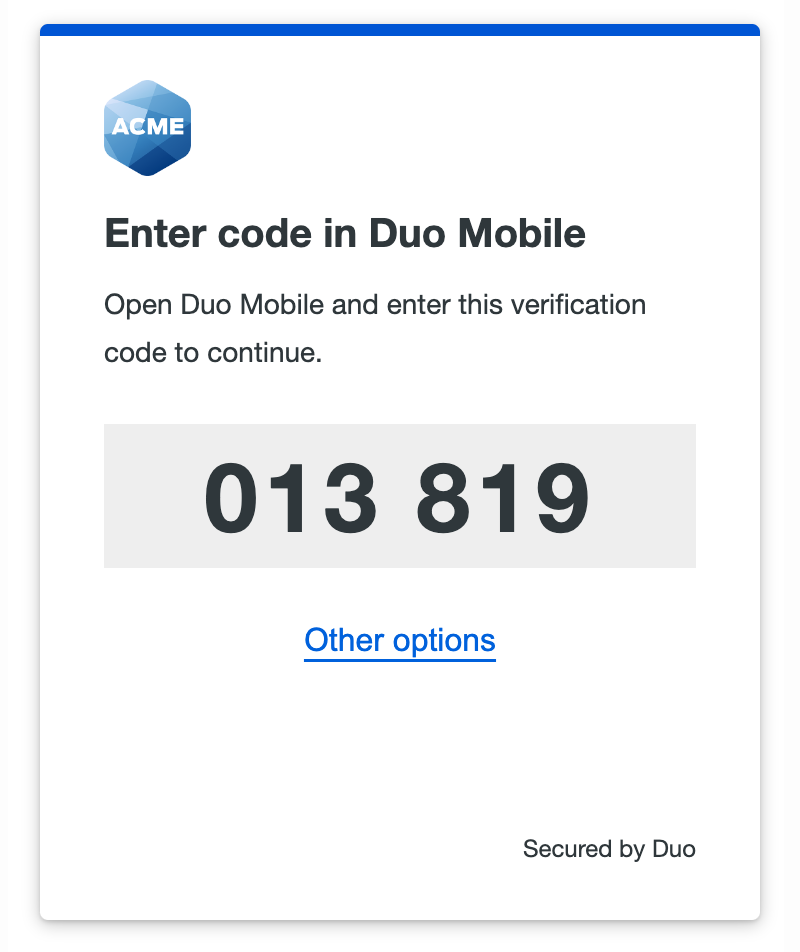
Next, you'll need to perform an additional verification step when approving the push request. After you enter the code from the browser prompt in Duo Mobile and tap Verify on the authentication request, perform Face ID verification or scan your enrolled finger at the Touch ID or Android fingerprint prompt to confirm the authentication approval. If you are unable to authenticate with a biometric factor you can fall back to your device's PIN or passcode.

When you successfully approve the Duo Push authentication with verification code and device biometric or PIN/passcode approval, you have the opportunity to remember your current device. If you remember the device now then next time you use Duo Push as the passwordless authenticator from that browser you will not need to enter the six-digit verification code; just device biometric or PIN/passcode verification while approving the Duo Push request. If you don't remember the device, future passwordless Duo Push authentication requests will require both the six-digit verification code from the Duo Universal Prompt and device verification to approve the login request.
If you clear the "known device" cookie from your access device's browser, log in from an Incognito or private browsing session that does not share or store cookies, use a different browser on the same access device, or switch to a different access device, then Duo Push won't be offered for passwordless authentication. We will only allow Duo Push passwordless authentication from access devices we recognize. You'll need to provide your password and approve a Duo Push two-factor authentication request to repeat the process of enabling Duo Push for Passwordless for the browser you're now using.
Log in with Password
There may be situations where you need to log in with your password after you've set up your Duo Passwordless authenticator, like if you need to access an application but don't have your passwordless authenticator with you. To do this, cancel the passwordless login in progress and then click or tap Show other options. Then you can select Password from the list of options and enter your password on the next screen.
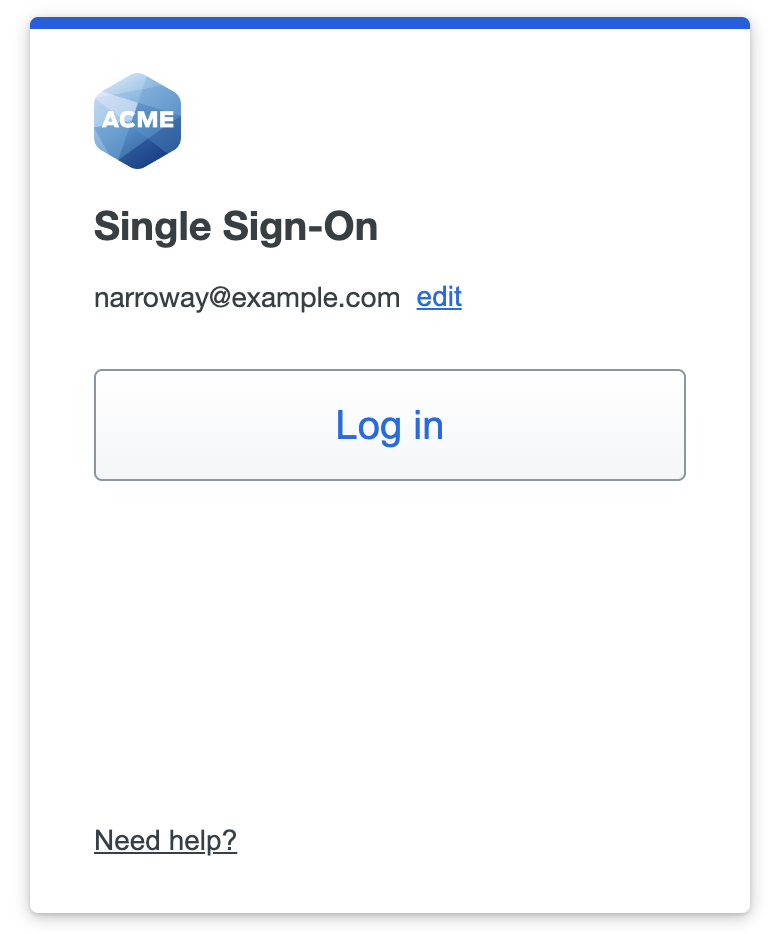
Change Remembered Username
Duo can remember your last-used username so you won't need to enter it again next time. You can click Log in to proceed. If you need to change the username click edit and enter the correct information.
Remembered Devices
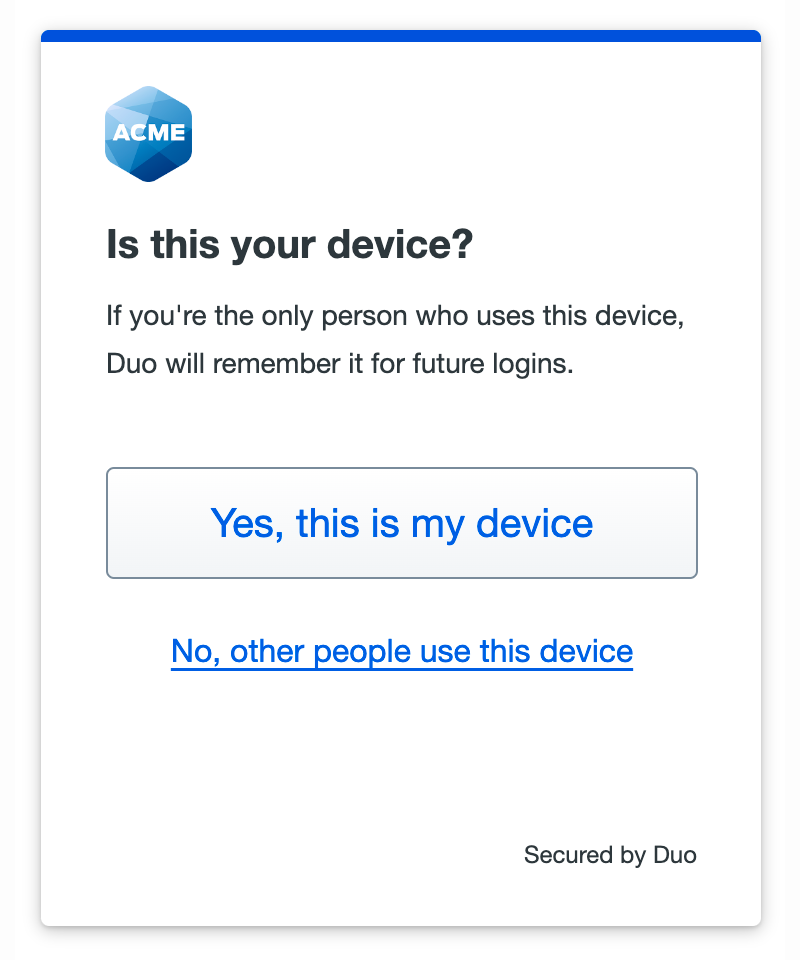
If your organization's policy allows it, you may be able to skip authenticating with Duo again for a set amount of time. The first time you approve the Duo authentication request, you'll see the option to remember your device.
Choose Yes, this is my device to create a trusted device session that will let you skip Duo two-factor authentication when you log in again with the same browser and device until that remembered device trusted session expires.
Depending on the policy applied by your Duo administrator, this may remember your device across all your organization's Duo-protected applications, or there may be unique policies applied to applications that require you to perform Duo authentication again regardless of whether you remembered the device. Ask your Duo administrator or help desk for more information.
Do not trust the device when using a public or shared computer! This could leave your Duo session available to other users. Remember the device only when you access applications from your own computer.
Clicking on No, other people use this device will not create a trust session. You won't be asked to remember that device again for 14 days.

When your trusted browser session expires, you will need to use your passwordless authenticator or password to log in again. After successful authentication you can once again opt to create a new remembered device session.
Set up Multiple Authenticator Types
If your organization allows both platform and roaming authenticators, you can set up both of them for your account (for example, if you want to be able to use either Windows Hello and a security key).
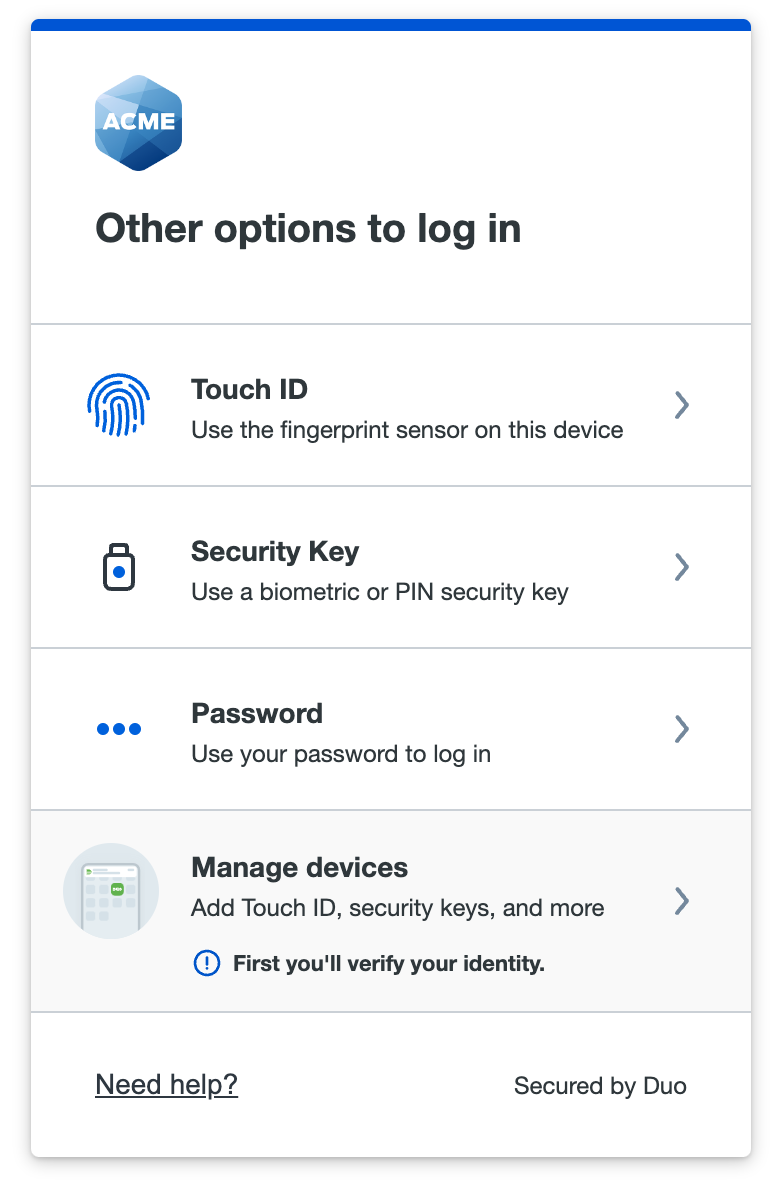
If your organization allows use of the Duo self-service portal you can add an additional passwordless authenticator there. Log into the application and when presented with the Duo Passwordless login option you can cancel and then tap or click the Need help? link at the bottom of the Duo authentication page. If your organization enabled self-service device management then you'll see a Manage devices link.
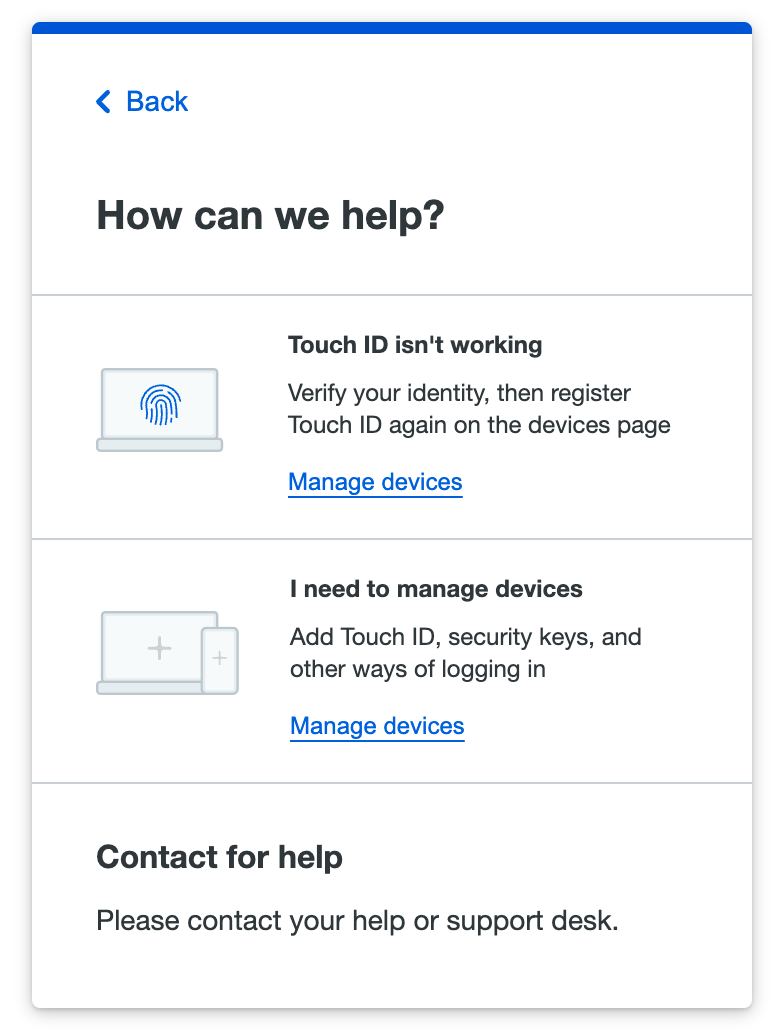
Click or tap that link and verify your identity with your existing passwordless authenticator or password to enter the device management portal. Then, you can click or tap Add a device to set up an additional passwordless authenticator.
If you don't see the Manage devices link then your organization doesn't allow use of the self-service device portal. Another way you can add more than one type of passwordless authenticator would be to log in with your password and complete set up of your platform authenticator in a regular browser tab, and then open an incognito or private browser window and log in with your password again, this time completing set up of a roaming authenticator.
Log in From a Different Device or Browser
If you set up a platform authenticator for passwordless logins (like Touch ID or Windows Hello), that verification method is associated with that device. If you switch to a different access device, you will need to log in with your password. After completing Duo two-factor authentication on the second device, you can set up the platform authenticator on that new device for Duo Passwordless logins.
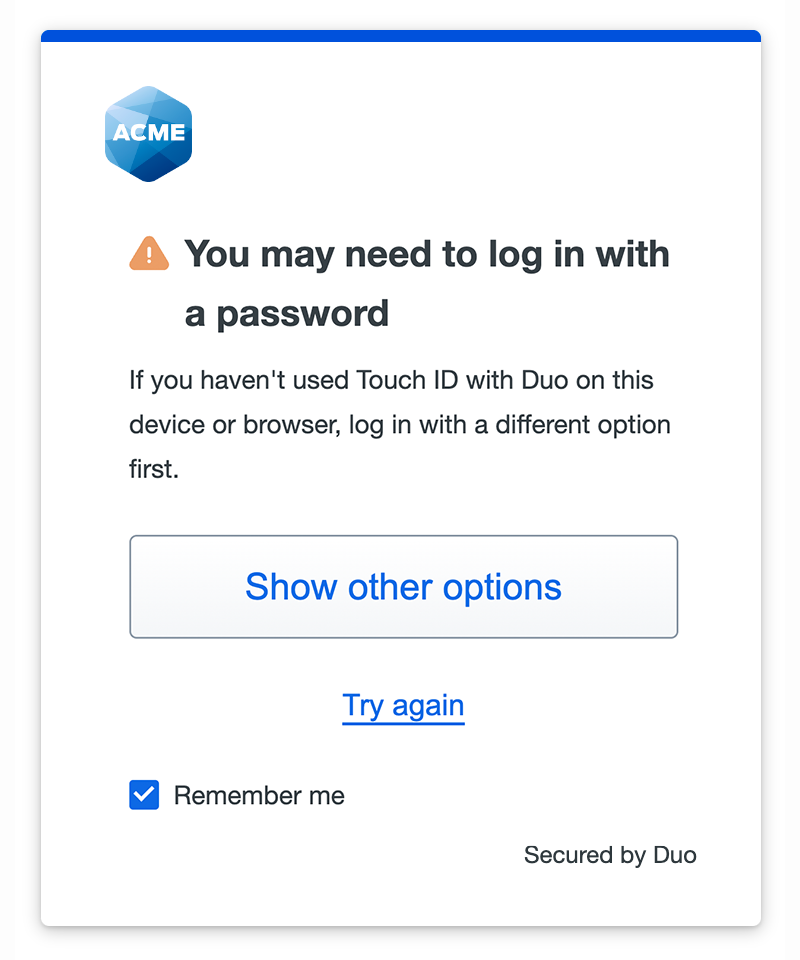
In some situations Duo Passwordless may think you are logging in from a different device when you use a different browser on the system where you already registered a platform authenticator (like if you set up Windows Hello from the Edge browser, but then switch to Firefox on the same computer). If this happens, Duo asks you to log in with a different authentication method.
If you aren't accessing the application from a new device, click or tap Try again to try your existing platform authenticator. Follow the prompts to verify your identity with your previously registered platform authenticator, and Duo logs you into the application without a password.
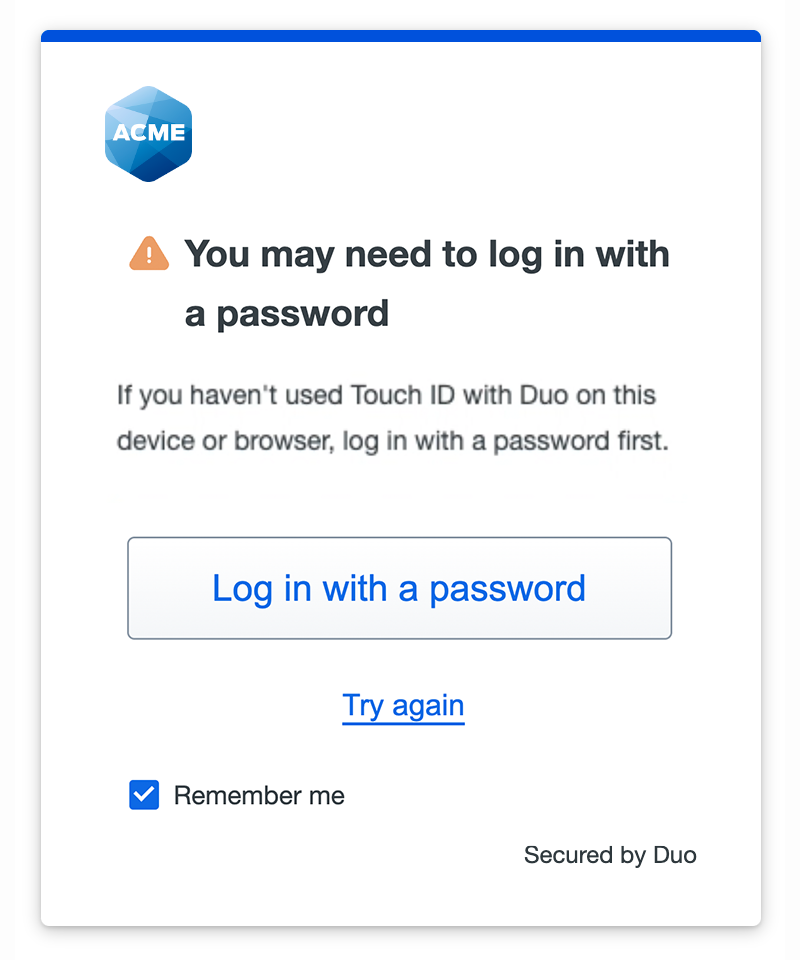
If you are accessing the application from a new device, click or tap the Log in with a password button. Enter your SSO password and then you can set up passwordless login on the new device.
Access Device Software Checks
Your Duo administrator may choose to warn you when your software is out of date, require software updates before allowing access, or even block access from devices that don't meet your organization's requirements.
Outdated Software
If the browser or operating system on the device you use to log into applications with Duo Passwordless fails your organization's health check, you'll see a notification prompting you to update your software.
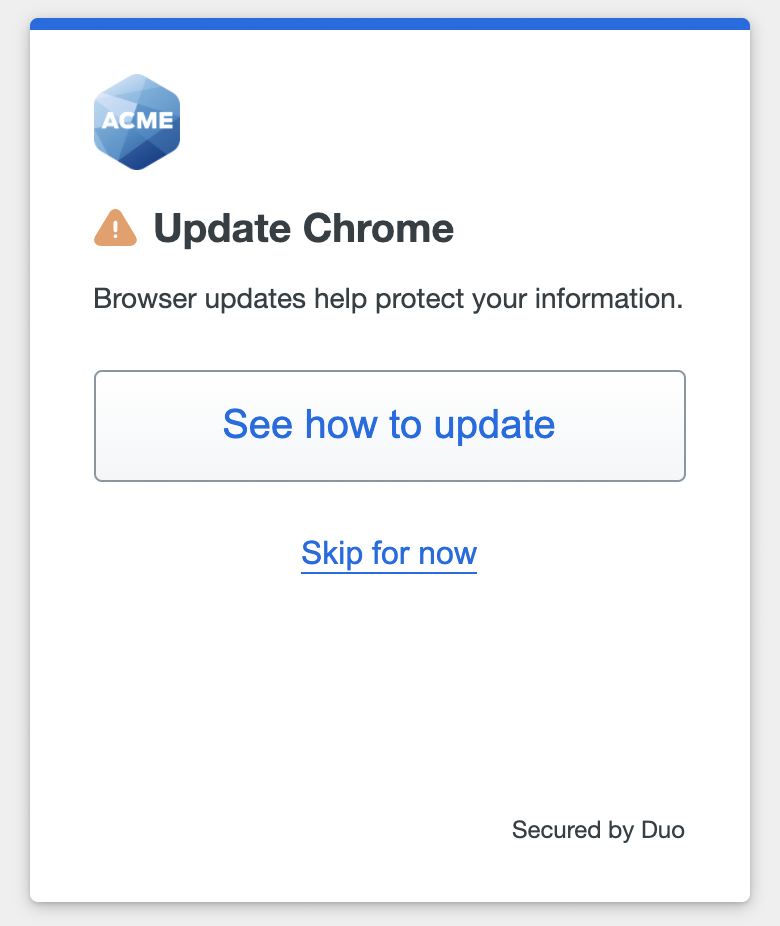
Click or tap See how to update for update instructions.
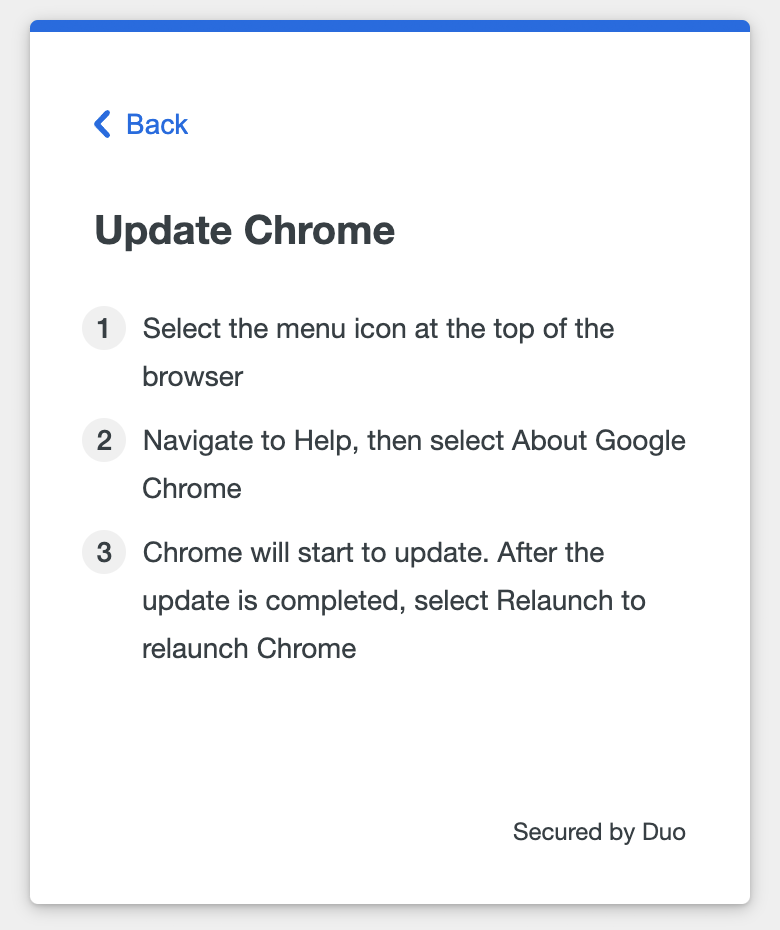
If your organization's policy allows you to access the application without updating your software, you can click or tap Skip for now to continue without updating.
If your organization requires up-to-date software to access applications, you won't see an option to skip past the notification and must update your browser or operating system. When your software is up to date you can try logging into the application again.

Blocked Software
If you try to access an application using an operating system or browser that your organization has blocked, you'll see a notification informing you that it isn't allowed.
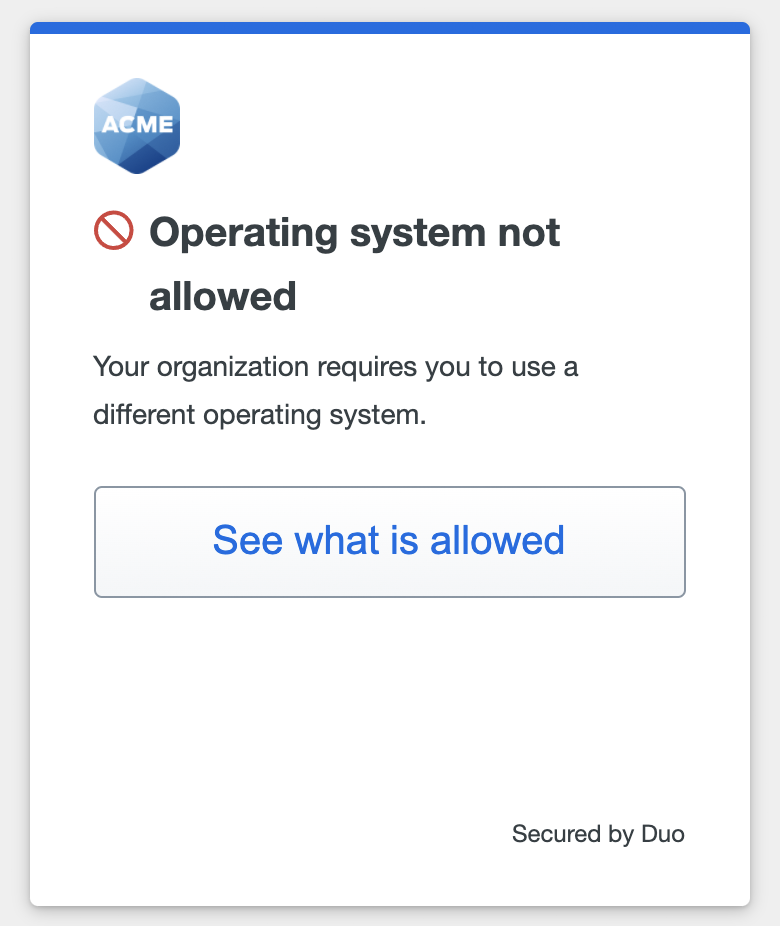
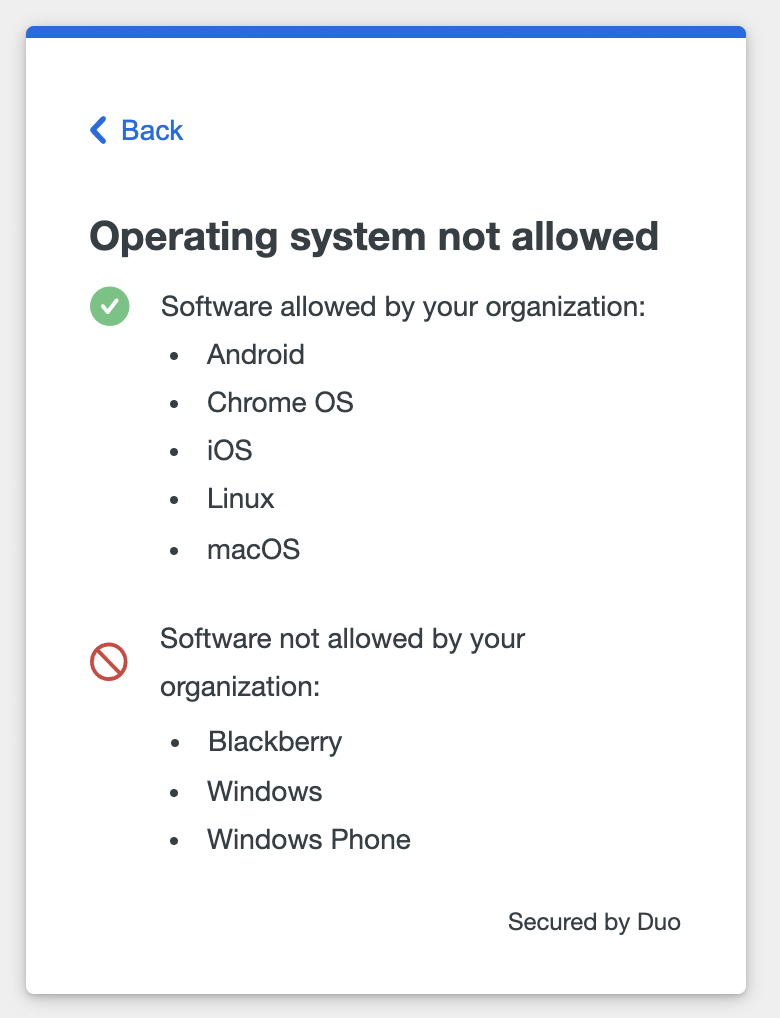
Click or tap See what is allowed for more details about which operating systems or browsers you may or may not use to access the application.
Device Verification with Duo Mobile
If you try to access an application from a mobile device, Duo may prompt you to verify your device identity with Duo Mobile. Tap Open Duo Mobile to open the Duo Mobile app on your phone and perform a device check. After device verification succeeds you can then use a platform or roaming authenticator or Duo Push to log in to the application.
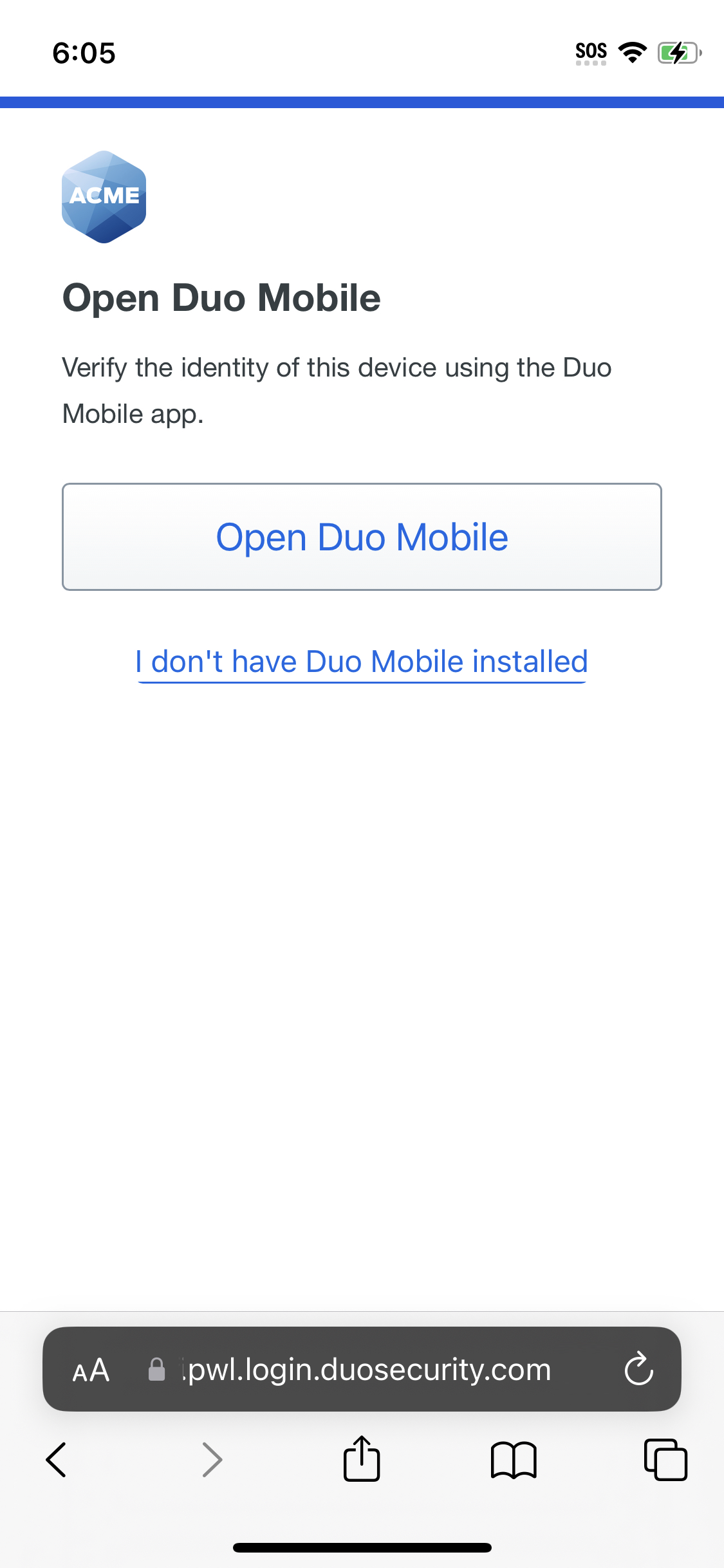
If you do not have Duo Mobile installed, tap I don't have Duo Mobile installed. This lets you complete Duo Passwordless authentication, but if your organization blocks access from unverified devices, you cannot access the application.

If you do have Duo Mobile installed but not activated for Duo Push then you can tap My account isn't activated to skip directly to Duo Passwordless authentication, but you may still be blocked by the trusted device check.
